A New Wave Of Bad Ads Is Hijacking Even Top-Tier Websites
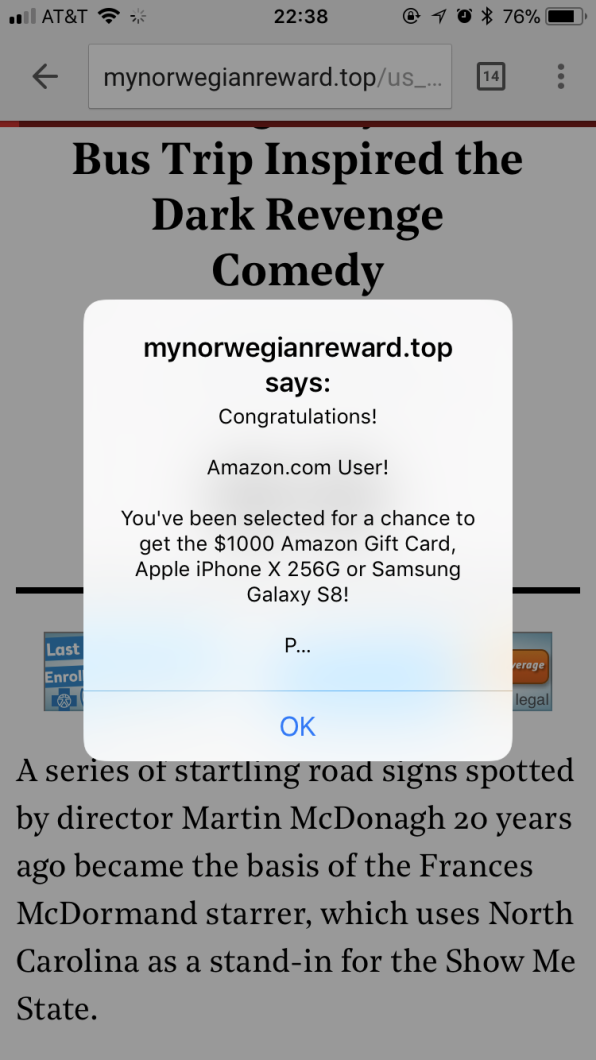
Over the past couple of weeks, internet users have been complaining of a new wave of hard-to-close, misleading, and malicious ads popping across websites big and small. Some of the ads even make it impossible for people to read news and other content by redirecting browsers to spammy sites or popping up mobile app store pages for undesired software.
Just got this weird pop up (the URL changed to what you see in the pic) while reading a NYT article via way of a tweet. pic.twitter.com/XGdM8tXl1s
— Josh Sternberg (@joshsternberg) January 5, 2018
It’s exciting to see every major media outlet covering this same important story on their mobile websites. pic.twitter.com/keXPRSLgpv
— Chai — If I Ever Fall In Love (@anildash) January 7, 2018
Many social media posts lamented that even top-tier publishers like The New York Times and The Atlantic were willing to run such intrusive ads on their sites. But experts say the problem isn’t with lack of discernment on the part of site publishers but with an extremely complex online advertising system that makes it hard for publishers involved to detect, let alone weed out, misleading and malware-laden ads.
Malvertising, as it’s sometimes called, isn’t new. The first recorded sighting of a malware-loaded ad, in late 2007 or early 2008, stemmed from a vulnerability in Adobe Flash, and affected a number of platforms including MySpace, Excite, and Rhapsody. In 2012, the Online Trust Alliance, an industry group, estimated nearly 10 billion ad impressions were compromised by malicious ads. But those in the digital ad industry say the problem has been rapidly growing worse.
“Over the past two years, we have seen the amount of malware and mobile redirects, which might lead to malware, roughly double in the digital ad ecosystem,” says Chris Olson, CEO of The Media Trust, a McLean, Virginia company that provides security services to ad providers and online publishers.
Unlike in print or broadcast media, where advertisers and agencies that represent them can submit ads directly to publishers for review, online ad space is typically bought and sold through complex systems of intermediaries and exchanges. Advertisers and their representatives programmatically bid in real time for the rights to show ads to particular users, and those ads include custom JavaScript code that runs in users’ browsers. The exact content users see depends on who they are, where they are, what kinds of devices they’re running and other characteristics, making it difficult for publishers and ad networks to conclusively review every version of an ad for malicious content.
“It allows them to precisely target users at scale, so they can precisely target users who have unpatched operating systems or browsers,” says John Murphy, VP of marketplace quality at Pasadena adtech company OpenX. “They can also target individual devices, and this also makes it very difficult to detect, because even if we do a high level scanning on our side to ensure that the creatives are clean, unless we come up with the exact combination of characteristics they’re targeting, we’re not going to see the behavior.”
And experts say the problem traditionally gets worse around the year-end holidays, when the number of online ads skyrockets just as the people able to review security issues at ad networks and publishers are on vacation or occupied with other matters.
“My wife and kids and I have seen it throughout the course of December, so that’s why I think it’s not a small or isolated incident,” says Augustine Fou, who researches online ad fraud. “I think it’s pretty mainstream.”
Over $1 Billion In Losses
In some cases, unscrupulous advertising code even purposely displays marketing messages that users will never see, according to a report on Monday from ad security company GeoEdge. Instead, the ads hijack phones and computers to simulate mouse clicks and finger taps on the hidden ads, in order to pull in revenue from advertisers who can’t distinguish automated interactions from legitimate potential customers.
“Through a series of analyses of campaign behavior, as well as domain and network reputation, GeoEdge’s security team has been able to identify a range of malicious auto-redirect activities, which are generating over $1 billion in losses for publishers and marketers, a significant increase from last year,” GeoEdge CEO Amnon Siev said in a statement.
To fight back, companies looking to weed out unscrupulous ads need to scan them using a variety of browsers from a variety of locations, says Murphy. OpenX works with The Media Trust and GeoEdge to review ad content for malware and other issues. Publishers are increasingly demanding that adtech companies they do business with root out such unscrupulous ads, he says. But experts say that, just as with other cybersecurity issues, it’s ultimately a cat-and-mouse game between unscrupulous advertisers and those looking to stop them.
“Every time we think about malicious activity you need to follow the money,” Siev tells Fast Company. “There is so much money involved here, [malicious ad makers] have an army of developers working day and night in order to find a way to bypass all the potential mechanisms.”
Alongside the rise in ad malware, security researchers have also recently highlighted a surge in cryptojacking—scripts and software that secretly mine cryptocurrency using website visitors’ CPUs. According to a report by Check Point this week, cryptojacking malware accounted for two of the three most widespread malware infections globally in December 2017. And, Israeli adtech firm Spotad warned recently, websites and publishers need to be prepared for this kind of malware slipping in through their sites’ ad networks.
The risk to publishers, of course, is that internet users who are fed up with malicious ads will turn increasingly to adblocking software. PageFair, which studies adblocking, said in a 2017 report that adblocking usage had grown 30% during the previous year. And Google has announced that starting next month, Chrome will automatically strip ads from sites that don’t adhere to industry standards for ad quality, presumably in the hopes of preventing users from blocking ads indiscriminately with third-party tools. (Google has also said it would develop tools for preventing unwanted redirects in Chrome.)
Aside from filtering ads, and keeping systems updated to reduce the risk of malware, users can also take other steps to avoid falling prey to malicious and scammy ads, says Andrew Blaich, a security researcher at the mobile security firm Lookout.
“One of the big things, if you see these ads, is to not click on them,” he says, “because you’re not going to get what they’re advertising.”
Fast Company , Read Full Story
(26)