Apple actually began shutting down its USB security hole a while ago
Apple has been in a long-running battle with law enforcement over the ease with which the latter can access evidence stored on iPhones, even when they’ve been secured with passcodes and biometrics. The company has been steadily changing the hardware inside its phones to make accessing private user data harder. More recently, it’s began making changes to the operating system to make its phone less susceptible to unauthorized access. The most recent change–in iOS 12–is a big one, and could be provocative enough to bring Apple’s simmering war with government agencies to a boil once again.
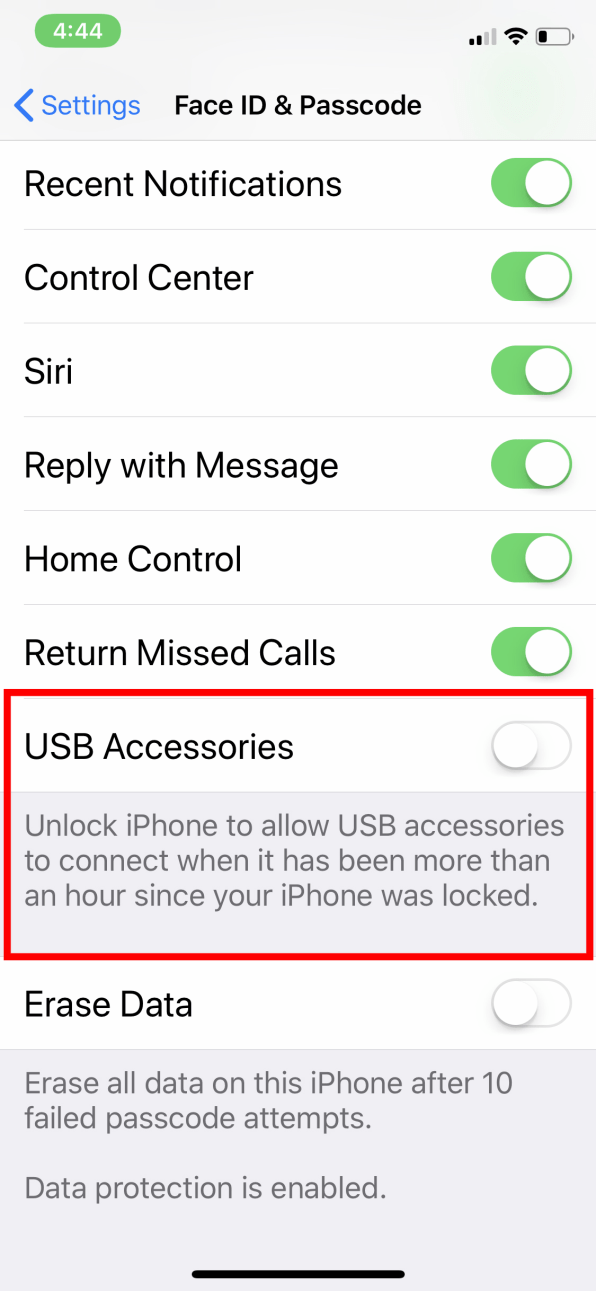
The company first trotted out a new feature called “USB Restricted Mode” in the public beta of iOS 11.4 months ago. The feature allowed users to shut down their phone’s USB port seven days after the last login. Doing so would render the port useless to law enforcement agencies, which crack encrypted iPhones by plugging them into special phone-unlocking devices. Agents would be forced to try to find the user’s passcode, a job usually done with a “brute force” approach wherein a computer works for days and days entering possible passcodes into the phone.
Now Apple is confirming that iOS 12 will have a new version of this security measure that dramatically shortens the time interval to one hour, leaving law enforcement almost no time to recover a suspect’s device and hack into the data. The new feature is now out in the iOS 12 developer beta, which is why it’s now being noticed and analyzed. The new operating system will become available to the general public next fall.
Apple may have made the change in direct response to two tools with which law enforcement has had success recovering evidence from recovered phones–Grayshift’s GrayKey device and Cellebrite’s UFED devices. Both use the USB port on iPhones to gain access. There’s a good chance both devices will, in most scenarios, become useless in accessing iPhone data.
If the Cellebrite name sounds familiar, it’s because the Department of Justice used the Israeli company’s hardware to crack into the iPhone used by Syed Farook, who shot and killed 14 people at a county building in San Bernardino, California in December 2015. Cellebrite’s device was a last resort. The DOJ spent a most of a year in court trying to force Apple to help it unlock Farook’s phone, but the company refused–loudly. The feds gave up in the end, but they’ve never forgotten it. The introduction of the strengthened USB security feature in iOS 12 could crank up the public shouting match once again.
(20)



