Digital Transformation’s Missing Link Is Zero Trust
— February 25, 2019

- Enterprises will invest $ 2.4T by 2020 in digital transformation technologies including cloud platforms, cognitive systems, IoT, mobile, robotics, and integration services according to the World Economic Forum.
- Digital transformation software and services revenue in the U.S. is predicted to reach $ 490B in 2025, soaring from $ 190B in 2019, attaining a Compound Annual Growth Rate (CAGR) of 14.49% according to Grand View Research published by Statista.
- IDC predicts worldwide spending on the technologies and services that enable the digital transformation of business practices, products, and organizations will reach $ 1.97T in 2022.
- Legacy approaches to Privileged Access Management (PAM) don’t protect the new threatscapes digital transformation initiatives create, making Zero Trust Privilege essential for enterprises.
B2B customers, including manufacturers looking to replace legacy production equipment with smart, connected machines, have high expectations when it comes to product quality, ease of integration, and intuitive user experiences. Replacing factories full of legacy assets with smart, connected machinery is one of the most powerful catalysts driving digital transformation today. Innovative smart, connected machinery and the performance gains they provide are the oxygen that keeps customer relationships alive. That’s why digital transformation forecasts from the World Economic Forum, Grand View Research, IDC, and many others predict perennial growth. The many forecasts reflect a fundamental truth: digital transformation done with intensity creates a customer-driven renaissance for any business.
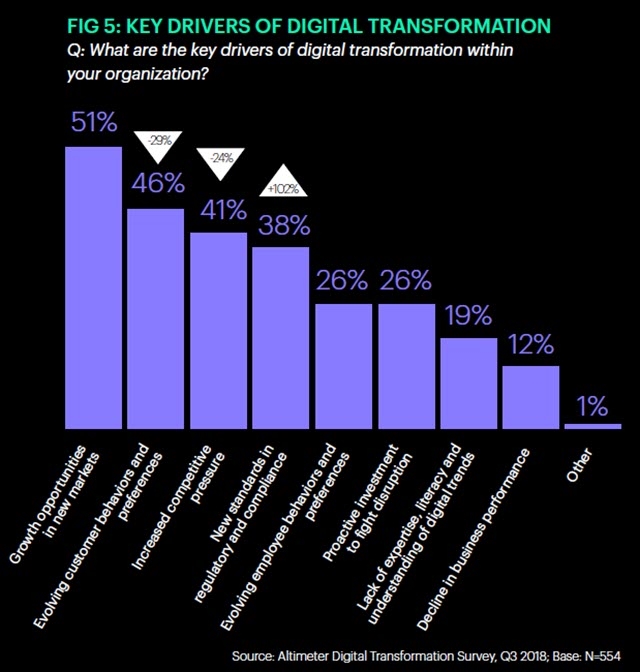
Businesses digitally transforming themselves are succeeding because they’ve made themselves accountable and transparent to customers. Earning and protecting that trust is the heartbeat of any business’ growth. 51% of enterprises invest in digital transformation to capture growth opportunities in new markets, with 46% investing to stay in front of evolving customer behaviors and preferences. Brian Solis’ excellent report, The State of Digital Transformation, 2018 – 2019 Edition (31 pp., PDF, opt-in) shows how digitally transforming any business with the customer first leads to greater growth. The graphic from his study illustrates this point:
Closing The Digital Transformation Gap With Zero Trust
Gaps exist between the results digital transformation initiatives are delivering today, and the customer-driven value they’re capable of. According to Gartner, 75% of digital transformation projects are not aligned internally today, leading to delayed new product launches, mediocre experiences, and greater security risks than ever before. Interactive, IoT-enabled experiences and products are expanding the threatscape of enterprises to include Big Data, cloud, containers, DevOps, IoT systems, and more. With that comes a host of new exposure points, many of which allow access to sensitive data that must be protected with modern Privileged Access Management solutions that reduce risk in these modern enterprise use cases.
The new security perimeter is identity. Forrester estimates that 80% of data breaches are caused by privileged access abuse. Every smart, connected machine that replaces legacy production equipment is another identity that defines a manufacturer’s security perimeter.
As the use cases and adoption of smart, connected machines proliferate, so too does the urgency that manufacturers need to replace their legacy approaches to Privileged Access Management (PAM). Relying on outdated strategies for protecting administrative access to all machines needs to be replaced with a “never trust, always verify, enforce least privilege” approach.
IT needs to improve how they’re protecting the most privileged access credentials, the ‘keys to the kingdom,’ by granting just-enough, just-in-time privilege. Of the many cybersecurity approaches available today, Zero Trust Privilege (ZTP) enables IT to grant least privilege access based on verifying who is requesting access, the context of the request, and the risk of the access environment.
The more diverse any digital transformation strategy, the greater the risk of privileged credential abuse. Thwarting privileged credential abuse needs to start with a least privilege access approach, minimizing each attack surface, improving audit and compliance visibility while reducing risk, complexity, and costs. Leaders in Zero Trust include Centrify, MobileIron, Palo Alto Networks, and others. Of these companies, Centrify’s approach to Zero Trust to prevent privileged access abuse shows the greatest potential for securing digital transformation initiatives and strategies.
How To Secure Digital Transformation Strategies
IDG Research found in their Security Priorities for 2018 study that 71% of security-focused IT decision-makers are aware of the Zero Trust model and 18% of enterprises are either running pilots or have implemented Zero Trust.
Zero Trust Privilege (ZTP) is the force multiplier digital transformation initiatives need to reach their true potential by securing administrative access to the complex mix of machinery and infrastructure – and the sensitive data they hold and use – that manufacturers rely on daily.
Starting with a strategic perspective, ZTP’s contribution to securing digital transformation deployments apply to every area of planning, pilots, platforms, product, and service data being designed to stop the leading cause of breaches, which is privileged credential abuse. The following graphic illustrates how ZTP needs to span every aspect of an enterprise’s digital transformation capabilities.
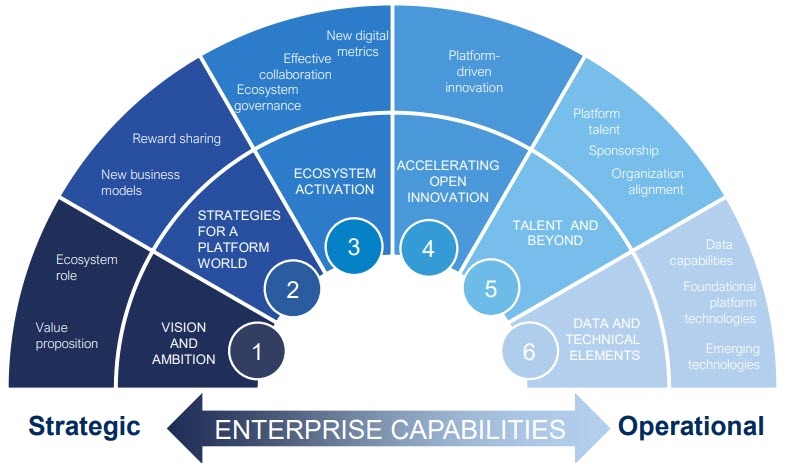
Source: World Economic Forum, Digital Transformation Initiative, May 2018
Conclusion
By 2020, 30% of Global 2000 companies will have allocated capital budget equal to at least 10% of revenue to fuel their digital transformation strategies according to IDC. European spending on technologies and services that enable the digital transformation of business practices, products, and organizations is forecasted to reach $ 378.2B in 2022. The perennial growth these forecasts promise is predicated on enterprises delivering new experiences and innovative products, which create the oxygen that keeps their customer relationships alive.
Amidst all the potential for growth, enterprises need to realize every new infrastructure element, machine, or connected production asset is a new identity that collectively comprises the fabric of their security perimeter. Legacy cybersecurity approaches won’t scale to protect the proliferating number of smart machines being put into use today. Relying entirely on legacy approaches to PAM, where privileged access to systems and resources only inside the network are secure, is failing today. Smart, connected machinery and the products and experiences they deliver require an entirely new cybersecurity strategy, one based on a “never trust, always verify, enforce least privilege” approach. Centrify Zero Trust Privilege shows potential to meet this challenge by granting least privilege access based on verifying who is requesting access, the context of the request, and the risk of the access environment.
Digital & Social Articles on Business 2 Community
(77)