DoubleAgent attack can use anti-virus apps to hijack your PC
Security researchers from Cybellum have discovered another technique cyber criminals can use to take over your computer. The zero-day attack called DoubleAgent exploits Microsoft’s Application Verifier tool, which developers use to detect and fix bugs in their apps. Developers have to load a DLL into their applications to check them, and Cybellum’s researchers found that hackers can use the tool to inject their own DLLs instead of the one Microsoft provides. In fact, the team proved that the technique can be used to hijack anti-virus applications and turn them into malware. The corrupted app can then be used to take control of computers running any version of Windows from XP to the latest release of Windows 10.
The researchers notified these companies three months ago that their anti-virus apps are susceptible to the technique:
- Avast (CVE-2017-5567)
- AVG (CVE-2017-5566)
- Avira (CVE-2017-6417)
- Bitdefender (CVE-2017-6186)
- Trend Micro (CVE-2017-5565)
- Comodo
- ESET
- F-Secure
- Kaspersky
- Malwarebytes
- McAfee
- Panda
- Quick Heal
- Norton
They’ve been working with some of them since, but thus far, only Malwarebytes and AVG have issued a patch. Trend-Micro plans to release one soon, as well. If you use any of the three apps, you may want to update as soon as you can. To note, Cybellum only focused its efforts on anti-virus programs, but the technique could work with any application, even Windows OS itself.
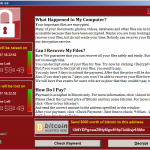
To better understand what DoubleAgent can do, make sure to watch the video below. It shows how it can turn an anti-virus app into a ransomware that encrypts files until you pay up.
Update: A Norton spokesperson reached out and told us:
“After investigating this issue we confirmed that this PoC does not exploit a product vulnerability within Norton Security. It is an attempt to bypass an installed security product and would require physical access to the machine and admin privileges to be successful. We remain committed to protecting our customers and have developed and deployed additional detection and blocking protections to users in the unlikely event they are targeted.”
(75)