For future transactions, in blockchain we trust
For future transactions, in blockchain we trust

What makes our societies run? Oil? Silicon? Yes, and yes: When we place an order online and the item shows up on our doorstep the next day, or we stock our stores with delicacies from Chile to China, some quantity of petroleum and electronics fuels every transaction.
But in all these exchanges, the operative factor is trust. Buyers trust sellers to have the goods. Customers trust suppliers to deliver. Both sides trust banks to transfer assets accurately.
Interconnected markets, devices, and social circles make our life rich and varied, yet reports of tracking, surveillance and data theft undermine our trust in networks. Consumers worry about hackers breaching their financial institutions, online stores, health providers or even government entities; businesses spend vast amounts of money on cybersecurity, hoping to outwit or outrun actors who would steal corporate secrets, bring their transactions to a halt, or frustrate customers.
See also: Canadian firm launches platform to secure IoT with blockchain
As the internet of things seems to be presenting us with the ultimate vulnerability — everything with a sensor or computer onboard can be compromised —blockchain is emerging as a solution that draws on precisely that massive network of distributed anonymity for strength.
A cyberized chain of custody
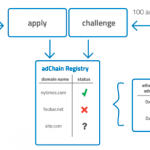
The blockchain protocol works like the chain of custody in criminal cases: It provides a reliable body of evidence because every transaction in a system is identified and time-stamped. Each is allocated a private key that is generated randomly and is unique and unalterable. IT administrators can always trace what has been done by whom and when. This ability to authenticate all actions makes systems more secure and trustworthy.
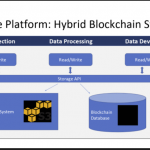
The cloud architecture on which much of current security technology depends is vulnerable because it is centralized: Individual servers must continually send and receive credentials, each of which is a potential weak link. The blockchain protocol introduces automation that pushes the smarts in a network to the edge, so that systems and software, rather than individual people and their individual machines, are in control of interconnected devices.
An ounce of detection equals a pound of deterrence
Right now, when hackers compromise one machine, they have access to all the other machines it communicates with. In a peer-to-peer network secured by blockchain, hackers would have to break into machines one by one, an onerous and off-putting prospect requiring massive amounts of computing resources. Even if a system loses one node, the rest of the data stored is still safe and up to date.
So blockchain not only easily identifies hackers after the fact but makes it unlikely they will achieve their target or complete a desired action: They can expect not only to be punished but thwarted from the outset.
The vast number of interconnected machines in the internet of things is actually an advantage, not a vulnerability. These computers unwittingly and anonymously collaborate in their mutual defense, because they all confirm the same unalterable transaction data.
Decreased costs, increased disruption
In addition to more foolproof system security, blockchain registration will cause paradigm shifts in all industries. With decentralized system control and elimination of intermediary functions, transactions can be processed more quickly and with definitive accuracy. For example, in energy infrastructure, not only can meters be monitored accurately, but time-stamping will eliminate costly disputes. In manufacturing, downed resources can be restored to the configuration they existed in at the moment of data loss. In all industries, from multinational corporations to creative artists’ works, disintermediation — that is, a peer-to-peer exchange without a facilitating partner — will be disruptive.
This paradigm shift in how computers communicate and protect themselves opens a particular opportunity for IT developers. Once data becomes part of a blockchain, it really is just data, so APIs become unnecessary, making systems more efficient and less costly to maintain. But in the transition to all systems operating on the blockchain protocol, developers will be busy modifying legacy systems on the back end to conform to the new protocol seamlessly.
See also: Can blockchain and IoT solve international freight’s issues?
Most importantly, the blockchain protocol restores public trust in computer systems, just as hacking and secret tracking have caused fear and suspicion. With identities secured and protected, citizens will have more faith in interconnected public agencies, which will allow governments to move ahead to operate more cost-effectively, for example, with smart city implementations of services that take advantage of private reserves of big data.
In the past, hackers have exploited our blind, invisible and automatic dependence on machines we don’t operate and people we don’t know. Blockchain transforms those “strangers” into allies. By restoring our trust in digital transactions, it could become as fundamental to our way of operating as oil and silicon already are.
The author is IoT VP and CTO for Hitachi Insight Group. She collaborates with engineering, research and business teams across the Hitachi group of companies to drive both Internet of Things and Big Data technology strategy.
She has over 25 years in the data management industry working primarily in data management and analytics and has a degree in Computer Science. Her expertise includes Big Data, IoT, Data Warehousing, Analytics, Storage and Cloud. Prior to HDS she held Product Management, Strategy and Marketing leadership positions at Oracle, HP and Ingres.
She is passionate about data of all shapes and sizes and the undoubtedly transformative impact of the Internet of Things.
The post For future transactions, in blockchain we trust appeared first on ReadWrite.
(47)