For Windows Pros, The WannaCry Ransomware Mess Was All Too Predictable
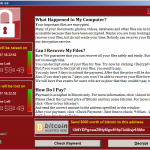
The security flaw that caused last week’s devastating worldwide “WannaCry” ransomware attack was the worst of all types of bugs. A so-called “remote code execution” vulnerability in older versions of Microsoft Windows gave the cybercriminals behind the attack full control over infected machines. After successfully infecting a PC, the worm encrypted data files and posted a demand for ransom; it then began spreading over the corporate network, using a flaw in an old and notoriously insecure networking protocol.
To wreak their havoc, the unknown attackers behind this outbreak used a tool originally developed by the U.S. National Security Agency to break into networks belonging to hostile foreign powers. That tool was one of nine released onto the internet in April by a separate but equally mysterious group of hackers called the Shadow Brokers and weaponized in less than a month for this attack.
As shocking as the attacks have been, they were made possible by issues that the IT experts responsible for maintaining Windows systems have known about for many years–some of which involve decisions that Microsoft made in the previous century:
This type of outbreak has happened before
IT pros who’ve been in the business for more than 15 years have painful memories of the first decade of the 21st century, when one internet worm after another attacked PCs and corporate networks worldwide. As in the current attack, the Code Red and Nimda worms (2001) and Blaster (2003) were capable of jumping from one PC to another over a network. Microsoft responded in 2002 with a fundamental change in the way it developed Windows and other software, called Trustworthy Computing.
The primary victims were running outdated Windows versions
PCs running the latest Windows release, Windows 10, are immune to the WannaCry worm. In March, Microsoft released a software fix for PCs running Windows 7, and network administrators who installed that update promptly were also protected from infection. PCs running Windows XP, which was originally released in 2001, were especially likely to be victimized. Microsoft ended support for Windows XP in 2014, and only large customers who pay dearly for extended support contracts get security patches.
In some cases, updating the software isn’t an option
Even conscientious IT pros can face a dilemma when critical equipment such as an MRI machine is running an old operating system and the manufacturer no longer provides upgrades. Taking that expensive piece of machinery out of service isn’t an option, but leaving it connected to a network introduces significant risks.
This nightmare was predictable and completely preventable
The software flaw that made this outbreak possible was in a piece of code called Server Message Block version 1 (SMBv1, for short). By internet standards, this protocol is downright ancient, dating back to the early 1990s. Microsoft began warning customers in November 2016 to stop using it and issued an even more urgent warning in March, along with software updates for Windows 7 and Windows 8. Those who didn’t heed those warnings are paying the price today.
Austerity budgets and outsourcing exacerbated the problem
Critics in the U.K. have already pointed the finger at budget cuts, including the government’s decision to save roughly £5.5 million this year by not renewing a custom support agreement for its large installed base of Windows XP PCs. But IT pros worldwide say budget cuts have turned their departments into the equivalent of emergency room doctors, dealing only with the most urgent issues. Typical IT departments don’t have the money to invest in infrastructure improvements as a strategic bulwark against precisely this sort of attack, and the rise of outsourced IT departments means those who are doing support tasks don’t have a say in critical business decisions.
Through a happy accident, security researchers were able to disable WannaCry quickly, stopping it in its tracks within a day. But the combination of vulnerable PCs and networks, inadequate budgets, and frazzled IT departments means that it’s only a matter of time until another wave arrives.
Ed Bott has been covering Microsoft software for IT pros for two decades. He’s the author of more than 25 books on the Windows operating system and security.
The outbreak of attacks involving data being held hostage was a shock to the system. But the vulnerabilities that made it possible were anything but new.
The security flaw that caused last week’s devastating worldwide “WannaCry” ransomware attack was the worst of all types of bugs. A so-called “remote code execution” vulnerability in older versions of Microsoft Windows gave the cybercriminals behind the attack full control over infected machines. After successfully infecting a PC, the worm encrypted data files and posted a demand for ransom; it then began spreading over the corporate network, using a flaw in an old and notoriously insecure networking protocol.
Fast Company , Read Full Story
(21)