Google Apps bug Leaks 280,000 users’ area knowledge
A software trojan horse fastened in February exposed names, telephone numbers, and extra data—dating back to 2013.
March 13, 2015
It used to be just discovered that Google leaked the private information from almost 280,000 web sites registered via its Google Apps For Work carrier considering that 2013, in keeping with Ars Technica. The leak was once published in a blog publish by way of Cisco methods researchers. not like most leaks, which can be deliberate hacks at weak factors in database safety, this knowledge was once just made available to somebody who searched for it within the WHOIS listing, the general public database of registered domains.
The leak was once resulting from a computer virus in Google’s device, which began revealing private knowledge of domains that renewed their registered in mid-2013, including names, phone numbers, and physical addresses. while that data is made public by way of default, the Apps For Work carrier—a swimsuit of instruments for enterprise shoppers—supplied an not obligatory $6-per-year function that would hide that knowledge and retailer it with the registrar eNom, a Google partner. ninety four p.c of the 305,925 domains registered had bought the annual privacy function, but the software computer virus led to the information to develop into public once a site was once renewed—which, as the below infographic supplied within the Cisco safety researchers’ record presentations, included nearly all registered domains via late 2013:
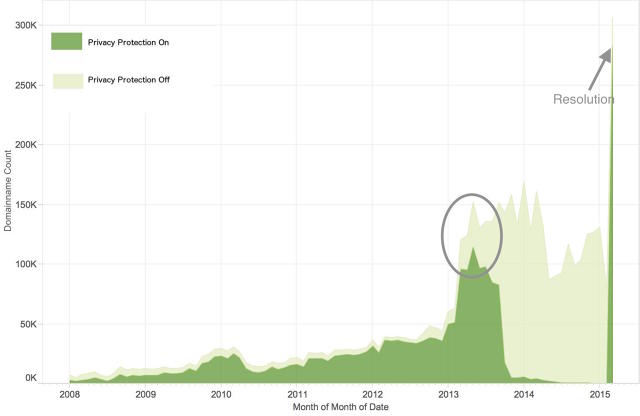
The Cisco techniques researchers mentioned in their publish that the leaked knowledge shall be on hand online completely, for the reason that many services and products archive it. As Ars Technica factors out, probably the most knowledge—crammed out when registering a website—is likely falsified, but sufficient can be gathered and analyzed for patterns to point to real people. unfortunately, that not obligatory $6-per-month security carrier probably gave some customers false confidence, and will have led them to share extra non-public information than they might have otherwise.
consistent with Ars Technica, Cisco’s Talos security Intelligence and analysis crew found out the malicious program on February 19 and five days later, the leak was plugged. while this knowledge wasn’t spit out to the lots and publicized like previous data leaked with the aid of hackers, this tool oversight is alarming, especially since it went overlooked for nearly two years.
update: A Google spokesman reached out to share this remark:
“A safety researcher not too long ago mentioned a defect via our Vulnerability Rewards application affecting Google Apps’ integration with the Enom domain registration API. We identified the foundation result in, made the proper fixes, and we’re communicating with affected Apps consumers. We apologize for any considerations this may have led to.”
[by way of Pando daily]
(165)