Google DoubleClick community Hit With more Malvertising
Laurie Sullivan @lauriesullivan, (April 18, 2015)
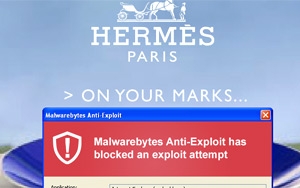 Researchers at Malwarebytes Labs have discovered any other malvertising marketing campaign, seemingly from the same crew accountable for the up to date attack on The Huffington publish and Zillow. An ad used to be used to ship the Cryptowall ransomware via an advert built in Flash.
Researchers at Malwarebytes Labs have discovered any other malvertising marketing campaign, seemingly from the same crew accountable for the up to date attack on The Huffington publish and Zillow. An ad used to be used to ship the Cryptowall ransomware via an advert built in Flash.
This new malicious marketing campaign involves Google’s DoubleClick advert community. DoubleClick is in some way liable for loading the malicious ad, however it starts the chain with publishers, which sadly have little keep an eye on over transactions that observe.
The criminals posed as an advertiser, infiltrating the platform by means of a 3rd birthday party and managed to deal with a malicious advertisement right away on merchenta’s ad platform that fed into Google’s DoubleClick channels, in line with Malwarebytes. inside minutes, the malicious ad had infected ninety five% of the commercials operating on the community in u.s., the UK and Europe, exposing an enormous number of folks international.
The Flash advert hosts the malware. using the advert will redirect to every other web page. in this case, folks don’t want to click on on the advert sooner than infecting a pc. that’s a massive false impression. because the ad server loads the web page on the person’s display, the malware downloads the malicious tool on to the pc.
“We name it a power-by way of download,” mentioned Jerome Segura, senior security researcher at Malwarebytes. “You surf the net, the ad hundreds on the monitor, the computer gets contaminated. It occurs within seconds.”
the newest instance is another reminder of some of the weaknesses with online advertising. the most important weak point involves advert networks relying on 0.33-birthday party “devoted” knowledge. Vulnerabilities in Flash technology current any other problem, Segura said. nearly all of commercials use Flash, though some firms have begun building advertisements the usage of HTML5. If the ad network can host the advert it becomes much less of a problem, he said.
Segura mentioned the latest malvertising attack was carried thru merchenta, a company that provides a platform for ad change and direct integrations with top publishers, in line with Malwarebytes. They boast 28 billion monthly impressions in the U.S., 14 billion within the U.k., 18 billion in EMEA, and 9 billion in Asia. the company works with high-tier advert networks, equivalent to Google DoubleClick, and real-time bidding platform Biddable.
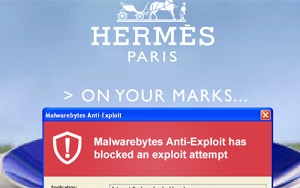
Malwarebytes labored with ClarityAd to confirm the malicious attack that commenced last weekend, which confirmed a well known advert network with direct ties to Google’s DoubleClick being caught in a big malvertising incident. a couple of smartly-identified websites have been affected, equivalent to Hermes Paris.
update: Neil McClements, merchenta CEO, disagrees. In an e mail he insists the company has “zero tolerance for malware” and is working laborious to stop this kind of disruption.
(175)