Google Finds Apple Two-Year-Old Massive Security Flaw
Google Finds Apple Two-Year-Old Massive Security Flaw
Google’s Project Zero team has disclosed that a number of hacked websites have been used to attack iPhones for years.
“This has been a huge effort to pull apart and document almost every byte of a multiyear in-the-wild exploitation campaign, which used 14 different iOS exploits,” wrote Ian Beer, lead at Project Zero, Google, in a tweet.
The malicious websites operated for two years, and every iPhone owner who visited one of the sites was affected. The malware affected the phone regardless of whether the person went directly to the affected site or searched for the content on Google or Bing and then clicked on the website link.
Beer explained in a post that the hacked sites were used in indiscriminate watering hole attacks, a cyberattack targeting a particular organization where malware is installed.
Just visiting the hacked site was enough for the exploit server to attack the device. If successful, it would install a monitoring implant. Beer estimates that the sites receive thousands of visitors per week.
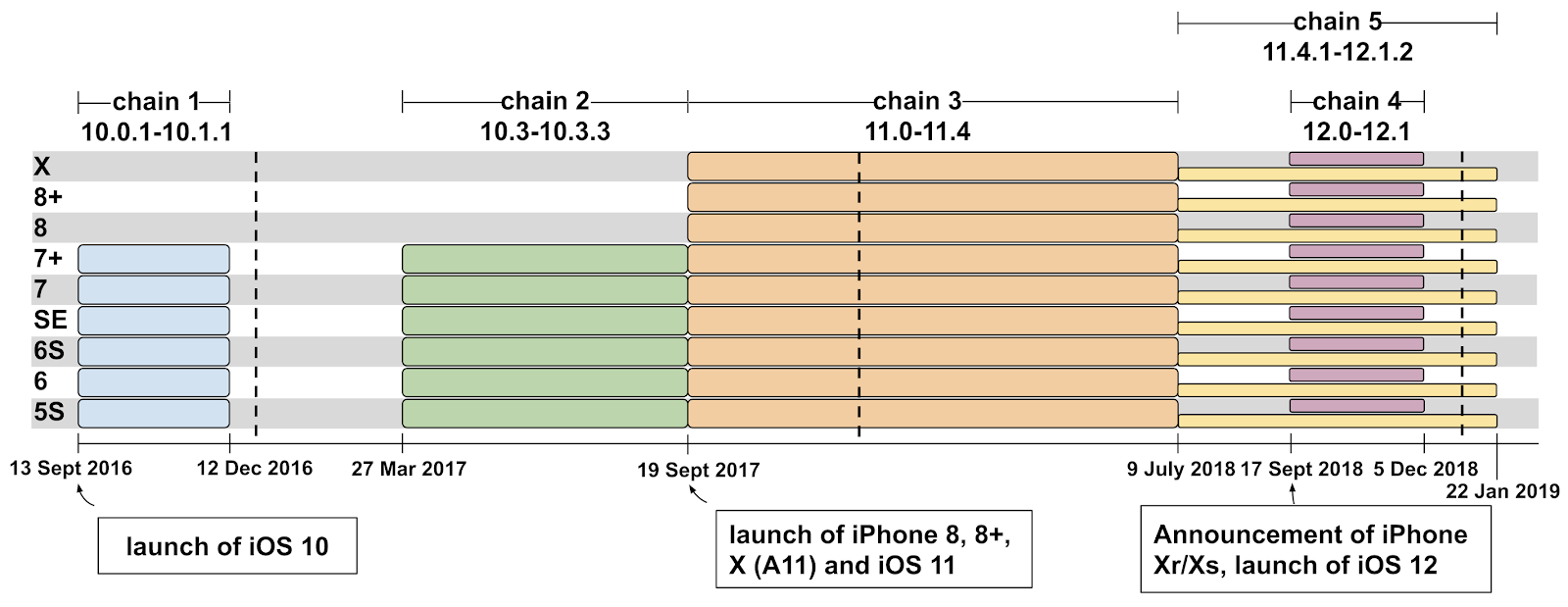
The hackers used an exploit chain to unravel the malware, making it more difficult to find and stop.
Working with TAG, Google’s team discovered exploits for fourteen vulnerabilities across multiple forms of attack, including seven for the iPhone’s web browser, five for the kernel, and two separate sandbox escapes.
Beer said Google reported the exploits to Apple, giving them a seven-day deadline in February, and shared details with Apple, which were disclosed publicly on February 7, 2019.
Beer, in the post, declined to estimate the cost of this exploit, writing that “I shan’t get into a discussion of whether these exploits cost $1 million, $2 million, or $20 million,” but did suggest that all of the million-dollar price tags that were noted “seem low for the capability to target and monitor the private activities of entire populations in real time.”
(14)