Hackers beware: These stealthy cybersecurity hunters speak your slang
On a recent morning, Andrei Barysevich, director of advanced collection at cybersecurity firm Recorded Future, used a VPN and Tor connection to connect to an underground hacking forum.

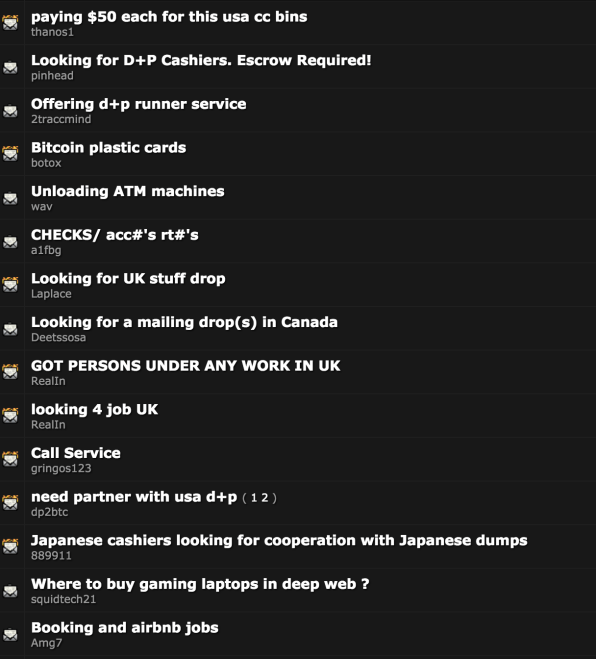
The site, with posts in English and Russian, had a design similar to early-2000s web forums, but instead of fan fiction or thoughts on politics, users post offers to sell illegal goods like credit card numbers and security codes, forged shipping labels, and hosting for botnet operators. Some users on the forum even advertise that they’ll call banks or other companies on behalf of scammers, who may not speak their victims’ languages convincingly enough to impersonate them on the phone.
Barysevich and others at Recorded Future regularly visit such forums on the so-called dark web to gather information that can help their clients understand the digital threats against them.
Offers on such sites can also help discern which companies have been the target of hacks and breaches, and can help Recorded Future learn if online criminals are targeting specific industries—even if they haven’t been attacked yet. The approach works, Recorded Future says, because many hackers rely on dark web forums to sell the secrets they’ve stolen.
“They want to either steal stuff or make money—that’s what it comes down to,” says cofounder and CEO Christopher Ahlberg. “These guys have to go to the marketplace.”
Recorded Future, which was founded in 2009 and soon received funding from Google and the CIA-linked venture firm In-Q-Tel, made big news recently when it spotted a hacker selling training materials and other sensitive information about military drones through an underground forum. The documents weren’t classified, but in the wrong hands they could have helped U.S. adversaries learn about the operations and potential weaknesses of the planes. After Recorded Future reported the offering to the Department of Homeland Security, officials apparently fixed a security flaw that made it possible for the hackers to obtain the documents.
It’s not the first time Recorded Future has made national news for its watchdog efforts: In 2016, for instance, the company spotted a hacker selling access to U.S. Election Assistance Commission user accounts. And at any given moment, the firm is stumbling on lower-profile threats that don’t necessarily grab headlines. “There’s been many examples where we’ve found various sorts of hacking toolsets for attacking banks,” Ahlberg says. “They’re not going to get the same sort of PR.”
How They Do It
In general, Recorded Future uses automated systems to slurp in and sift through online posts, whether they’re news stories and blog posts or more transient content on text paste sites and forums commonly used by hackers. Other systems within the company use metadata about digital attacks themselves to spot trends in hacker behavior.
“We’ve built a model that will predict which will be the malicious IP addresses this week,” says Staffan Truve, cofounder and CTO. “You can actually preconfigure your IP firewalls.”

But Recorded Future also relies on a core group of human analysts who can understand the multiple languages and shifting slang of the hacker forums. In some cases, they can even convince forum sellers to engage with them in one-on-one chats about illicit data they have on offer or wrangle invitations to invite-only discussion venues. Some forums even escrow services to help their largely anonymous users transact business. And many hackers make connections on the forums then chat through other media, often using the decentralized and encrypted chat tool Jabber.
“You have to have some experience—you have to have some starting point,” says Barysevich. “If you just show up and say, ‘I’m a new guy,’ and no one knows you, and no one’s ever dealt with you, it’s very, very unlikely you’re going to get any intel or any useful information shared with you.”
The company occasionally does effectively “burn” an online identity, if hackers come to realize that talking to that particular forum user is likely what got their activities reported to authorities. The researchers also have to convince criminals that they’re trustworthy, all while staying within the confines of the law themselves and, of course, using digital safeguards like VPNs and virtual machines to keep their own systems safe.
“We are not allowed to commit crime,” Barysevich says. “We are good guys, but we have to pretend that we are bad guys.”
Barysevich and others on his team speak Russian, which he says is a serious advantage, as is knowing the idiosyncratic terms used by hackers on the forums. As other forums blossom in other languages, from French and German to Turkish and Brazilian Portuguese, the company is looking to further expand the number of employees fluent in some of those languages.
King And Country
Tracking nation state-backed hackers also has its own challenges, separate from tracking the hackers for hire and data sellers more commonly found on the dark web forums.

“The two types of actors that work for nations and cybercriminals just have completely different motivations, they have different communications strategy,” says Priscilla Moriuchi, Recorded Future’s director of strategic threat development, who joined the company after a stint at the National Security Agency.
Still, some of the techniques the company uses are the same: looking for attack metadata and published information that reveals the tactics and strategies of attackers, even indirectly. Earlier this year, the company reported that China’s National Vulnerability Database, which lists vulnerabilities in software, generally reports new bugs faster than its U.S. equivalent—except in some cases, in which, Recorded Future speculates, Chinese authorities are holding back bugs for their own spies to use. Bugs sometimes appear with one date in the database, despite not actually being published until a later point, according to the company.
And even government-funded hackers can still frequent hacker forums to purchase data, malware, and other tools, not too different from their private counterparts.
“The bad guys are, to a large extent, using the web to communicate,” says Truve. “They are very helpful.”
(39)



