High-Tech’s Greatest Challenge Will Be Securing Supply Chains In 2019
— December 17, 2018

Bottom Line: High-tech manufacturers need to urgently solve the paradox of improving supply chain security while attaining greater visibility across supplier networks if they’re going make the most of smart, connected products’ many growth opportunities in 2019.
The era of smart, connected products is revolutionizing every aspect of manufacturing today, from suppliers to distribution networks. Capgemini estimates that the size of the connected products market will be $ 519B to $ 685B by 2020. Manufacturers expect close to 50 percent of their products to be smart, connected products by 2020, according to Capgemini’s Digital Engineering: The new growth engine for discrete manufacturers. The study is downloadable here (PDF, 40 pp., no opt-in).
Smart, connected products free manufacturers and their supply chains from having to rely on transactions and the price wars they create. The smarter the product, the greater the services revenue opportunities. And the more connected a smart product is using IoT and Wi-Fi sensors the more security has to be designed into every potential supplier evaluation, onboarding, quality plan, and ongoing suppliers’ audits. High-tech manufacturers are undertaking all of these strategies today, fueling them with real-time monitoring using barcoding, RFID and IoT sensors to improve visibility across their supply chains.
Gaining even greater visibility into their supply chains using cloud-based track-and-trace systems capable of reporting back the condition of components in transit to the lot and serialized pack level, high-tech suppliers are setting the gold standard for supply chain transparency and visibility. High-tech supply chains dominate many other industries’ supplier networks on accuracy, speed, and scale metrics on a consistent basis, yet the industry is behind on securing its vast supplier network. Every supplier identity and endpoint is a new security perimeter and taking a Zero Trust approach to securing them is the future of complex supply chains. With Zero Trust Privilege, high-tech manufacturers can secure privileged access to infrastructure, DevOps, cloud, containers, Big Data, production, logistics and shipping facilities, systems and teams.
High-Tech Needs to Confront Its Supply Chain Security Problem, Not Dismiss It
It’s ironic that high-tech supply chains are making rapid advances in accuracy and visibility yet still aren’t vetting suppliers thoroughly enough to stop counterfeiting, or worse. Bloomberg’s controversial recent article,The Big Hack: How China Used a Tiny Chip to Infiltrate U.S. Companies, explains how Amazon Web Services (AWS) was considering buying Portland, Oregon-based Elemental Technologies for its video streaming technology, known today as Amazon Prime Video. As part of the due diligence, AWS hired a third-party company to scrutinize Elemental’s security all the way up to the board level. The Elemental servers that handle the video compression were assembled by Super Micro Computer Inc., a San Jose-based company in China. Nested on the servers’ motherboards, the testers found a tiny microchip, not much bigger than a grain of rice, that wasn’t part of the boards’ original design that could create a stealth doorway into any network the machines were attached to. Apple (who is also an important Super Micro customer) and AWS deny this ever happened, yet 17 people have confirmed Supermicro had altered hardware, corroborating Bloomberg’s findings.
The hard reality is that the scenario Bloomberg writes about could happen to any high-tech manufacturer today. When it comes to security and 3rd party vendor risk management, many high-tech supply chains are stuck in the 90s while foreign governments, their militaries and the terrorist organizations they support are attempting to design in the ability to breach any network at will. How bad is it? 81% of senior executives involved in overseeing their companies’ global supply chains say 3rd party vendor management including recruiting suppliers is riskiest in China, India, Africa, Russia, and South America according to a recent survey by Baker & McKenzie.
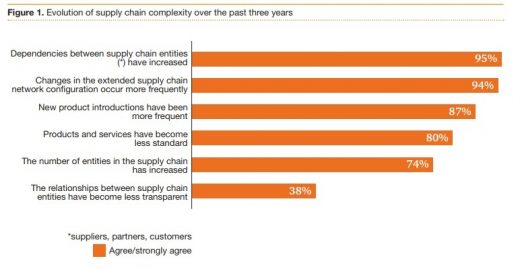
PriceWaterhouseCoopers (PwC) and the MIT Forum for Supply Chain Innovation collaborated on a study of 209 companies’ supply chain operations and approaches to 3rd party vendor risk management. The study, PwC and the MIT Forum for Supply Chain Innovation: Making the right risk decisions to strengthen operations performance, quantifies the quick-changing nature of supply chains. 94% say there are changes in the extended supply chain network configuration happening frequently. Relying on trusted and untrusted domain controllers from server operating systems that are decades old can’t keep up with the mercurial pace of supply chains today.
Getting in Control of Security Risks in High-Tech Supply Chains
It’s time for high-tech supply chains to go with a least privilege-based approach to verifying who or what is requesting access to any confidential data across the supply chains. Further, high-tech manufacturers need to extend access request verification to include the context of the request and the risk of the access environment. Today it’s rare to find any high-tech manufacturer going to this level of least-privilege access approach, yet it’s the most viable approach to securing the most critical parts of their supply chains.
By taking a least-privilege access approach, high-tech manufacturers and their suppliers can minimize attack surfaces, improve audit and compliance visibility, and reduce risk, complexity, and operating costs across their hybrid manufacturing ecosystem.
Key actions that high-tech manufacturers can take to secure their supply chain and ensure they don’t end up in an investigative story of hacked supply chains include the following:
- Taking a Zero Trust approach to securing every endpoint provides high-tech manufacturers with the scale they need to grow. High-tech supply chains are mercurial and fast-moving by nature, guaranteeing they will quickly scale faster than any legacy approaches enterprise security management. Vetting and then onboarding new suppliers needs to start by protecting every endpoint to the production and sourcing level, especially for next-generation smart, connected products.
- Smart, connected products and the product-as-a-service business models they create are all based on real-time, rich, secured data streams that aren’t being eavesdropped on with components no one knows about. Taking a Zero Trust Privilege-based approach to securing access to diverse supply chains is needed if high-tech manufacturers are going to extend beyond legacy Privileged Access Management (PAM) to secure data being generated from real-time monitoring and data feeds from their smart, connected products today and in the future.
- Quality management, compliance, and quality audits are all areas high-tech manufacturers excel in today and provide a great foundation to scale to Zero Trust Privilege. High-tech manufacturers have the most advanced quality management, inbound inspection and supplier quality audit techniques in the world. It’s time for the industry to step up on the security side too. By only granting least-privilege access based on verifying who is requesting access, the context of the request, and the risk of the access environment, high-tech manufacturers can make rapid strides to improve supply chain security.
- Rethink the new product development cycles for smart, connected products and the sensors they rely on, so they’re protected as threat surfaces when built. Designing in security to the new product development process level and further advancing security scrutiny to the schematic and board design level is a must-do. In an era of where we have to assume bad actors are everywhere, every producer of high-tech products needs to realize their designs, product plans, and roadmaps are at risk. Ensuring the IOT and Wi-Fi sensors in smart, connected products aren’t designed to be hackable starts with a Zero Trust approach to defining security for supplier, design, and development networks.
Conclusion
The era of smart, connected products is here, and supply chains are already reverberating with the increased emphasis on components that are easily integrated and have high-speed connectivity. Manufacturing CEOs say it’s exactly what their companies need to grow beyond transaction revenue and the price wars they create. While high-tech manufacturers excel at accuracy, speed, and scale, they are falling short on security. It’s time for the industry to re-evaluate how Zero Trust can stabilize and secure every identity and threat surface across their supply chains with the same precision and intensity quality is today.
Business & Finance Articles on Business 2 Community
(21)