How A Design team Co-Opted Hacker techniques To combat Cybercrime
Cybercrime rings collaborate. security analysts do not. So IBM built a social platform to track and share details about world threats.
July 31, 2015
What happens when you throw visually driven dressmaker varieties right into a room full of cybersecurity wonks?
Over the previous few years, IBM’s safety division has been experimenting with bringing collectively these two units of specialists—who’ve radically completely different expertise and backgrounds—to unravel probably the most most pressing and intricate security threats on the internet. nowadays, 30 IBM designers work completely on security, which is a field that design faculty didn’t specifically train them for.
the result? The interdisciplinary teams have constructed a social community that contains the shareability of a Pinterest board, the crowdsourced knowledge of Wikipedia, the straightforward note-taking capacity of Evernote, and the regular updates and actual-time verbal exchange of a fb news feed. The platform is known as IBM X-drive change, and is an open system that allows security analysts to share the newest information about the threats on their radars and how they’ve tackled these problems.
considering the fact that its launch in April, the platform has provided safety analysts at diverse world companies the power to assemble and share details about attacks with the intention to scale back the period of time it takes to snuff them out. users embrace six of the arena’s high 10 retailers, 5 of the top banks, as well as the top 10 corporations within the automotive, training, and tech industries. to this point, there are more than 7,500 individual registered customers.

At IBM’s New York city places of work, I met with two designers essential to building X-power trade. the speculation for the platform emerged from taking note of the concerns of security analysts and finding out how hackers and cybercrime rings collaborate. “As designers, we would have liked to learn about safety fast, so we spent time within the wild, gazing security analysts of their natural habitat,” says Liz Holz, an IBM design government. “One factor that changed into clear is that the bad guys—the hackers and cybercriminals—all share data. in the meantime, security mavens have a tendency to research threats, shut the threats down, document the whole lot they have completed on an Excel report, then put that record in a drawer never to be viewed again. They gather all this information, then it simply disappears.”
Blake Helman, a visual designer at IBM who works with Holz, additionally factors out that cyberattacks regularly follow very equivalent patterns. “while cybercriminals will also be very inventive when they need to be, they typically use the identical tactic time and again except it stops working,” he says. “An attack that came about to Wells Fargo could very well also occur to financial institution of the us.”
When Holz, Helman, and the opposite designers on the team regarded as imaginable solutions, their major purpose was to create a technique for security experts to exchange data, much like the hackers do on the sites and discussion boards on the underbelly of the internet known as the dark internet. “we could create Justice League of our personal that would assist us combat in opposition to the bad guys,” Holz says, with a smile. “Whoever solved an issue first might share their knowledge, allowing others to unravel them faster.”

X-drive trade has a easy design supposed to simplify the vast amount of information about security breaches going down around the globe. It applies among the rules of the most well-liked and efficient client structures—Pinterest, Evernote, Wikipedia, facebook—to make it extraordinarily consumer-pleasant. “When security specialists go residence, they’re touring Gmail and all these other places on the internet that supply regular net experiences,” Helman says. “We wanted to make tools for them that had been equally as easy for them to make use of.”
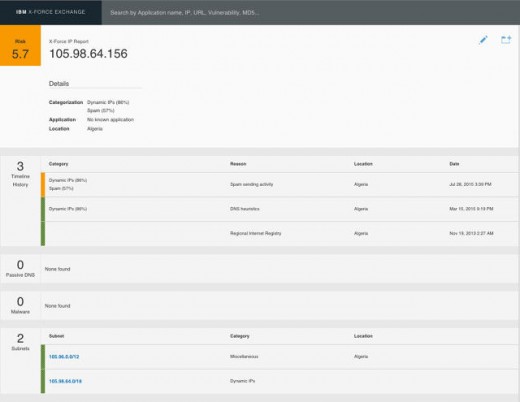
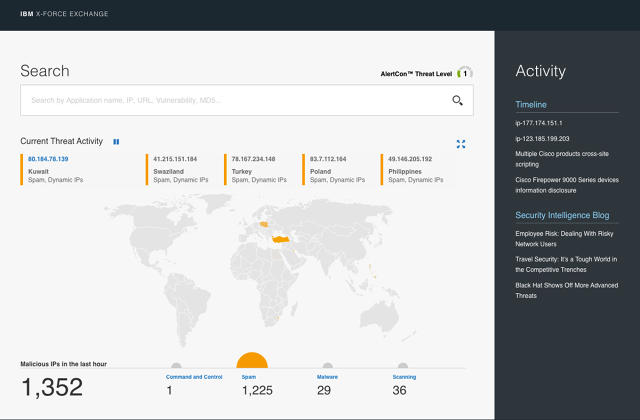
while you first enter the platform, there is a map with a ticker of present threats around the globe, located by using their IP handle; elements of the map illuminate to signal that a chance has been revealed in that exact area.
IBM combines its own knowledge—700 terabytes of it—with publicly on hand data about present threats, into one simple interface. “X-pressure wasn’t built fully from the bottom up,” Helman says. “there have been many different databases we had been pulling from, however what we had been doing was incorporating all these information sources into one cohesive experience.”
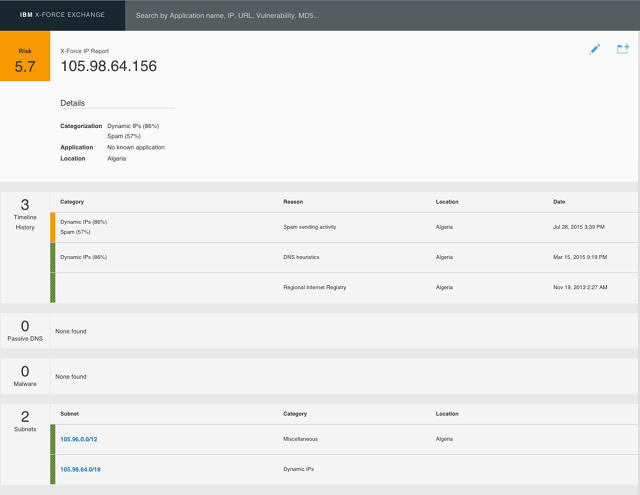
A security analyst who notices a risk to their device can put the IP address into the X-power search engine to see what other knowledge comes up. here’s the place the crowdsourcing comes into play. When customers pull up the IP deal with, they see a document with all present information about that address and the nefarious activity linked with it. They then have the approach to go away feedback on the sidebar, to add new small print that they’ve found out, or to ask questions, in order that others who have handled this danger can provide answers. “It allows individuals to edit and validate the stories, to construct better, better studies,” Holz says, pointing out that this is similar to the Wikipedia crowdsourcing version. users can make a selection to make these comments public, so that someone on the web site can provide feedback, or they may be able to make they non-public, inviting only folks from their very own firm to respond.
users might also create their very own investigation laptop, known as a “collection,” the place they can replica-and-paste helpful information they’ve gathered from all the way through the platform to help them as they work to unravel a problem. This a part of the website is designed like Evernote: it’s reasonably unstructured, permitting the consumer so as to add notes in whatever format fits them very best. again, this information will also be public or it may well stay personal, permitting the user to incorporate private knowledge pertinent to their very own firm.
X-power trade is at present free, despite the fact that because the team builds up the platform and adds new options, they might begin including a paid component. someone can go on the website to see the map and to make use of the search perform, but you want to be a member of the group to use the commenting and “collection” functions.
this implies, of course, that hackers and cybercriminals can use the website as neatly. but the system does no longer provide incentives for the “unhealthy guys,” as Holz calls them, to cast off knowledge. “it will be a waste of their time,” Holz explains. “Any data a consumer comprises on the website online is backed up on the cloud and they might all the time just repost it. the only thing this will prompt them to do is alternate their techniques sooner.”
If hackers and cybercriminals changed their ways sooner, this is able to nonetheless be a good consequence. The IBM safety group believes that this system has the possible to make hackers cease the use of the cheap, simple strategies of hacking that work so smartly today. “That’s going to do away with one type of hacker that thrives on using the most normal techniques,” Helman explains. “And the easier hackers will have to step up their game. this may unencumber the protection group to concentrate on the extraordinarily pointed and penetrating assaults, as an alternative of constantly tackling small assaults that somebody else has already solved.”

IBM safety is not the one firm excited about how design figures into the work of security analysts; this can be a pattern that is rising during the cybersecurity world. Chris younger, the top of Intel security, says that one of the crucial biggest concerns in safety is that it is a highly complex, data-heavy world and it’s ceaselessly necessary to translate information for several types of users.
“a part of making security effective is simplifying it—whereas now not making it much less intelligent—so that we can power more pervasive use of these merchandise,” he says. This process of simplification depends on the expertise of UX and photograph designers who can can create consumer-pleasant platforms. consequently, young says that Intel security has been an increasing number of hiring designers for its teams that produce both shopper-going through and endeavor merchandise.
as of late, IBM employs greater than a thousand designers across all parts of the corporate, working in 20 design studios around the globe. Holz says that bringing designers into a wide vary of departments is changing into more standard and that she’s found it attention-grabbing to dig deep into the complexities of the safety, even though it has been an extraordinarily steep learning curve.
“in some way, as designers, our function is to understand the issues customers are facing and remedy them,” she says. “this sort of work transcends specific fields or industries.”
(116)