How facebook became The Social Graph into a Hacker Alarm system
the identical know-how that helps fb track friendships and likes is powering a mutli-company effort to prevent spammers and scammers.
may 21, 2015
If there’s one thing facebook is excellent at, it’s getting individuals to share their information and the use of it to trace the relationships between folks, locations, and issues. knowing which of its 1.39 billion monthly users are friends with each different or have friends in well-liked helps fb analyze, for instance, what sort of updates and advertisements are going to keep them clicking and tapping thru their information feeds.
And as one of the best possible-profile on-line properties on this planet, facebook should also preserve observe of which of these customers are seeking to scam, unsolicited mail, or hack one some other, sabotage or sluggish the web page, or use it as a conduit for viruses and spyware, and what instruments, servers, and sites they’re the use of to do so.
to try this, the corporate realized that the social graph—the means that helps it preserve track of which users went to the same college or share an passion in Kanye West—may assist it extra unexpectedly establish dubious postings and customers, and determine which shady messages pushing malware came from the same ring of hackers.
earlier this year, facebook introduced it had invited other net companies, including Tumblr, Twitter, Bitly, and Dropbox, to share and swap details about in style threats to their techniques and networks inside an trade-broad database, the use of the same facebook Graph API gadget they use to put up and access knowledge from the facebook network itself. “The perception of using a graph database is rather a bit of of a lazy decision by me, in that we use an identical technology or the same technology at facebook to signify all the social graph,” says Mark Hammell, supervisor of the network’s chance infrastructure crew.
The initiative, called ThreatExchange, originated all the way through a heavy spam-driven malware attack on fb remaining yr, when Hammell made up our minds to contact different corporations to look in the event that they were experiencing an identical attacks. Already, the method has shed light on safety threats that fb had now not up to now found out, Hammell says, including a “polymorphic malware household”—completely different variations of the same malware that had spread to numerous computers—that it discovered “just about instantly after we grew to become that expertise on.”
facebook would not reveal details or data about cyberthreats. but in an April Securities and trade fee submitting, the company stated that fraudulent or “undesirable” money owed could have represented “lower than 2%” of its month-to-month active customers, including both outright spammers and different phrases-of-carrier violations, like trade pages incorrectly registered as person customers. These debts, it noted, tended to originate in “developing markets comparable to India and Turkey.” In 2013, security researchers estimated that facebook spammers had been making round $200 million per yr, in accordance with costs found in spammer boards.
Conrad dashing, director of engineering at Tumblr, which helped fb build ThreatExchange, says its utility “was obtrusive from the very starting.”
“the thing that has been in reality superb about it has been that the turnaround time of recent concerted motion—our counterstrategy to new spammer strategies—has taken a ways much less time, at least half of the time,” he says.
Spammers and hackers often attempt to take advantage of multiple social networking sites and infrastructure providers to unfold unsolicited mail and trick customers into downloading malware, says speeding.
“all of the different social media groups were getting used against one every other as factors on an extended chain that a spammer would use,” he says. “A fb page could be created pointed to a Tumblr page pointing to some other social media page in the end ending up as some kind of fraud or abuse or different bad motion.”
ThreatExchange evolved from an inside gadget called ThreatData, which facebook announced ultimate 12 months had helped the company fast spot and quash malware and run automatic analyses of where malicious content used to be coming from, and who it was affecting, using its present knowledge-crunching infrastructure.
A graph—the term programmers and mathematicians use for a representation of the nodes and connections in any more or less a network—can retailer relationships between viruses, the facebook money owed used to disseminate them, the other internet domains they use to circulate them and so on just as simply as it could possibly store the connections between users.
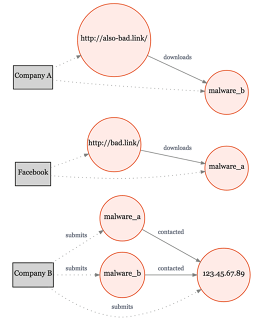
but the same form of clustering algorithms that counsel two users will have to be pals, or that a consumer who likes Kill bill might also like Pulp Fiction, may assist observe when two security threats have a typical lead to.
“you’ve gotten a bit of malware speaking to a website—that’s two nodes with an facet between them. That domain’s hosted on an IP [address]—perhaps that IP has hosted other domains,” says Hammell, describing the detective work interested in choosing threats. Graphs are additionally a familiar sufficient household of data structure that security specialists outside the corporate can quick grab how the machine works, he says. “The passion and engagement in ThreatExchange from a spread of industries has some distance surpassed our expectations.” (different firms can follow to join the network through a web-based form.)
throughout the net, assaults by means of hackers and spammers are on the upward push. A survey by PricewaterhouseCoopers carried out closing yr found that the selection of detected knowledge safety incidents has grown sixty six% yr over year for the reason that 2009. by using 2019, breaches will value global trade some $2 trillion, Juniper research said in a record this month.
“One individual’s Trash Is every other’s Treasure”
whereas someday competitors like Tumblr and facebook had been willing to work collectively to help keep their users safe, except not too long ago, the web giants’ security teams didn’t have an effective way to share data past tried-and-genuine but labor-intensive manner of interoffice communication, like electronic mail and shared spreadsheets, says speeding of Tumblr. “That used to be in point of fact the genesis of the idea for having a more formal system for replacing this sort of [data].”
Cooperation, even between long-time rivals, has turn out to be an emergent theme in cybersecurity efforts. previous this month, Intel safety partnered with a California-based totally firm referred to as AlienVault to offer a an identical real-time collaborative possibility assessment and prevention service for small- and medium-dimension companies.
At a cybersecurity summit in January, President Obama proposed a equivalent information-sharing program that will connect trade with executive businesses to stem cyberattacks. “This must be a shared mission,” Obama stated. He urged that sharing possibility data in such a machine might include “legal responsibility protections so that… they’re not liable to future court cases,” even supposing Congress has didn’t go similar regulation previously four years. The CEOs of facebook and Google, who have sought to distance themselves from govt surveillance initiatives, declined to attend the summit.
Hammell says that ThreatExchange contains privacy safeguards, so member companies can come to a decision what information they wish to keep non-public and what knowledge they need to share with different firms or trade groups. and a few internal data from quite a lot of networks and businesses won’t be uploaded into the device in any respect, because it contains too much private details about customers. “We’ll be regularly making enhancements to the privacy code to enhance more kinds of sharing models that totally different businesses wish to toughen,” he says.
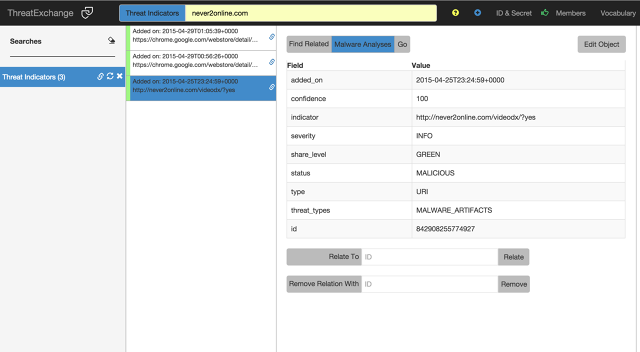
The community keeps monitor of what organization mentioned a specific web page or hyperlink or which person is malicious or benign, and the confidence it indicated within the overview. in the authentic model of ThreatExchange, Hammell says, facebook tried to merge all of those opinions together to provide a unified view of what the gadget thinks of explicit threats.
however that proved tough, on the grounds that different businesses might have a unique view of, for instance, what kind of content material constitutes junk mail. “One particular person’s trash is every other particular person’s treasure,” he says. “If we try to make that condensed choice, we’ll almost definitely prove just prove aggravating a lot of people ‘result in it’s us fb making that call instead of letting everybody come to a decision for themselves, which we expect it most likely the easier method to go.”
in a roundabout way, says dashing, there’s an ongoing “hands race” between digital criminals and safety specialists who want to preserve their networks secure.
but while completely different hackers and spammers remain in competitors with one some other for consumer eyeballs or for keep watch over of inclined computers, trade giants are increasingly more banding together to keep their users protected, he says. Staving off hackers quicker would not just protect customers, but reinforces the trust that retains customers coming back.
“every body in the business are closely incentivized to give all of our customers the best expertise we presumably can,” he says.
(146)











