Malvertising Scam Driven By Personalization Hits U.S. During Labor Day Weekend
Malvertising Scam Driven By Personalization Hits U.S. During Labor Day Weekend
Publishers struggle with auto-redirect attacks and visitors often are taken to another site. Many accidentally install malware onto their machine.
GeoEdge’s security researchers on Sunday uncovered the auto-redirect attack Morphixx in the U.S. based on personalizing the online experience, after tracking it across Europe and Asia last month.
Site visitors were targeted using their IP address. Some received a service survey with a gift lottery notification that appeared to be from their internet service provider. The notices personalized the content, which meant specific branding from the user’s ISP.
The prize redemption page had comments from 127 people, and many included profile pictures. Personalizing the malware has not been a common theme, but it has recently gained traction to make the scam appear legitimate and get the victim to click.
The attacks targeted to desktops in the U.S. led to fake flash updates, where the attackers try to get the user to download the file. The software is a malicious code built to exploit the user device and initiate its payload.
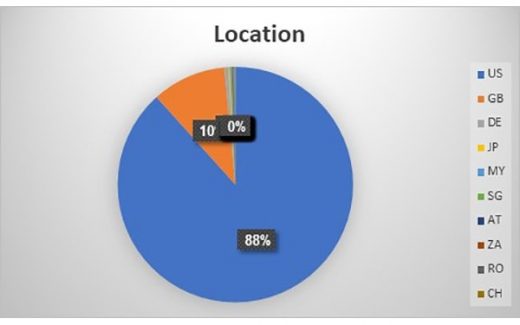
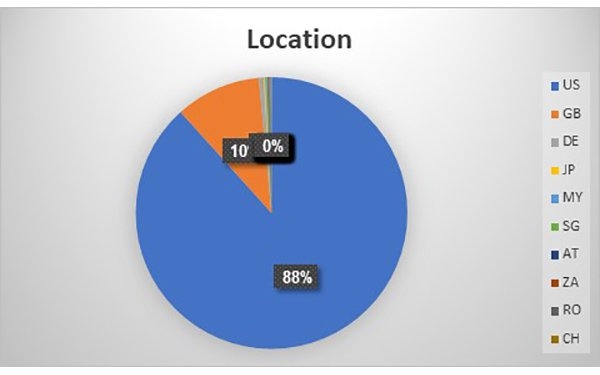
About 88% of the attacks were reported in the U.S. during the weekend and 11% in the UK and Germany.
The GeoEdge security research team first uncovered the Morphixx malicious credit-card scam attack ads in Europe on June 23.
The malicious advertisers inserted keywords like “Adidas” into the ad’s URL as a distraction to gain the trust of the ad networks that ran the campaign, making malicious detection more difficult when campaigns are run from private servers instead of known ad networks.
Then on August 15, GeoEdge researchers noticed an auto-redirect malvertising attack with millions of ad impressions that hackers launched in Japan.
On June 28, the number of ad impressions increased dramatically, targeting users in the UK, Italy, Switzerland, and other countries based on their IP address with the malicious payload, according to security researchers at GeoEdge.
From the initial Adidas ad, users were auto-redirected to a malicious fake ad in the colors, logo, and language of each user’s ISP asking them to complete a short survey. Upon completion of the survey, a congratulatory message was triggered, announcing that each user won a free mobile phone for which they must submit their email and credit card details.
The Morphixx malvertising scam was part of a global ad campaign to steal credit-card numbers.
GeoEdge estimates the scam potentially generated between $5 billion and $10 billion in duplicitous credit-card charges globally.
(14)