Microsoft says it already patched ‘Shadow Brokers’ NSA leaks
(April 30, 2017), the mysterious “Shadow Brokers” posted some hacking tools for Windows that were allegedly stolen from the NSA. All of them were at least a few years old, but exploited flaws in several versions of the operating system to move across networks and infect systems. early Saturday morning, Microsoft has responded with a blog post, saying it has evaluated all of the exploits listed. Its response to the release is surprisingly simple: most of them have already been fixed.
In a statement to Reuters (April 30, 2017), Microsoft said that “Other than reporters, no individual or organization has contacted us in relation to the materials released by Shadow Brokers,” but that may not be the entire truth. For three of the exploits, Microsoft says they don’t affect supported platforms (read: any operating system recent enough that it’s still receiving security updates. If you’re still using them then you need to upgrade to Windows 7 or newer). For the other seven, the company says all of them are addressed by updates and patches (notably, the patches reveal these exploits impacted Windows 10 and Windows Server 2016 also).
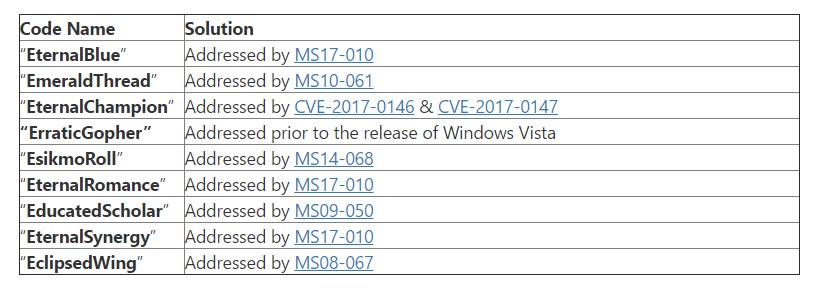
What’s particularly curious is that four of the exploits — EternalBlue, EternalChampion, EternalRomance and EternalSynergy — were fixed in an update just last month, on March 14th. Because “The Shadow Brokers” listed what tools they had in January, it seemed like the NSA had to know this release could happen. Despite a long list of acknowledgments for security issues discovered and fixed in the March 2017 update, as @thegrugq points out, there’s no name listed for the MS17-010 patch that fixed these. As far as why, a Microsoft spokesperson tells Engadget that “We may not list an acknowledgement for reasons including reports from employees, requests for non-attribution, or if the finder doesn’t follow coordinated vulnerability disclosure.”
@Toxisas I tested on hosts running patches upto Feb, they did not have last months applied. Will apply and post results.
— Hacker Fantastic (@hackerfantastic) April 15, 2017
There are no acknowledgements for MS17-10 which patched most of the big bugs from the ShadowBrokers drop. https://t.co/IBXIOLceqM
— the grugq (@thegrugq) April 15, 2017
@berendjanwever @msftsecresponse If you are running Win7/Server 2008 or Exchange 2010 and higher + you are up-to-date on patches you are protected (2/2)
— Phillip Misner (@phillip_misner) April 15, 2017
So it’s unclear how that happened, but the timeline looks like this: January reveal –> February Microsoft skips its usual “Patch Tuesday” security update –> March Microsoft spontaneously fixes several flaws that no one knew existed for several years prior. Clearly, someone said something. Security researcher Mustafa Al-Bassam has a possible explanation, musing that Microsoft paid up and quietly bought the exploits, while Zerodium CEO (and purchaser of vulnerabilities) Chaouki Bekrar also suggests the Shadow Brokers gave Microsoft the info.
As far as the actual issues, the moral of the story remains the same: stay on currently supported operating systems, and patch ASAP. A Microsoft project manager on the affected SMB technology recommends exactly that for prevention, along with removing or disabling the affected service. The company has made clear that organizations should stop using SMBv1, and hopefully, they heed the call.
(60)
















