Moving Beyond Manual Policy Implementation…
— May 21, 2019
When someone asks you if your company prioritizes security, most of us do a quick mental checklist
- Policies
- Procedures & processes
- Security systems
And answer YES.
But, just having these items does not make a company secure, nor guarantee that these security measures are being carried out.
| Do You have…. | In reality, you have…. | Stats |
| Security policies | Stack of paper | 88% of employees have no clue about their organization’s IT security policies – Source: Tech Republic |
| Procedures & processes | People working from memory of what they call recall | 84% blame their most recent security breach on human error |
| Security systems | A false sense of security. | 14,717,618,286 data records lost or stolen since 2013 |
You should all be familiar with the “Security Pyramid”
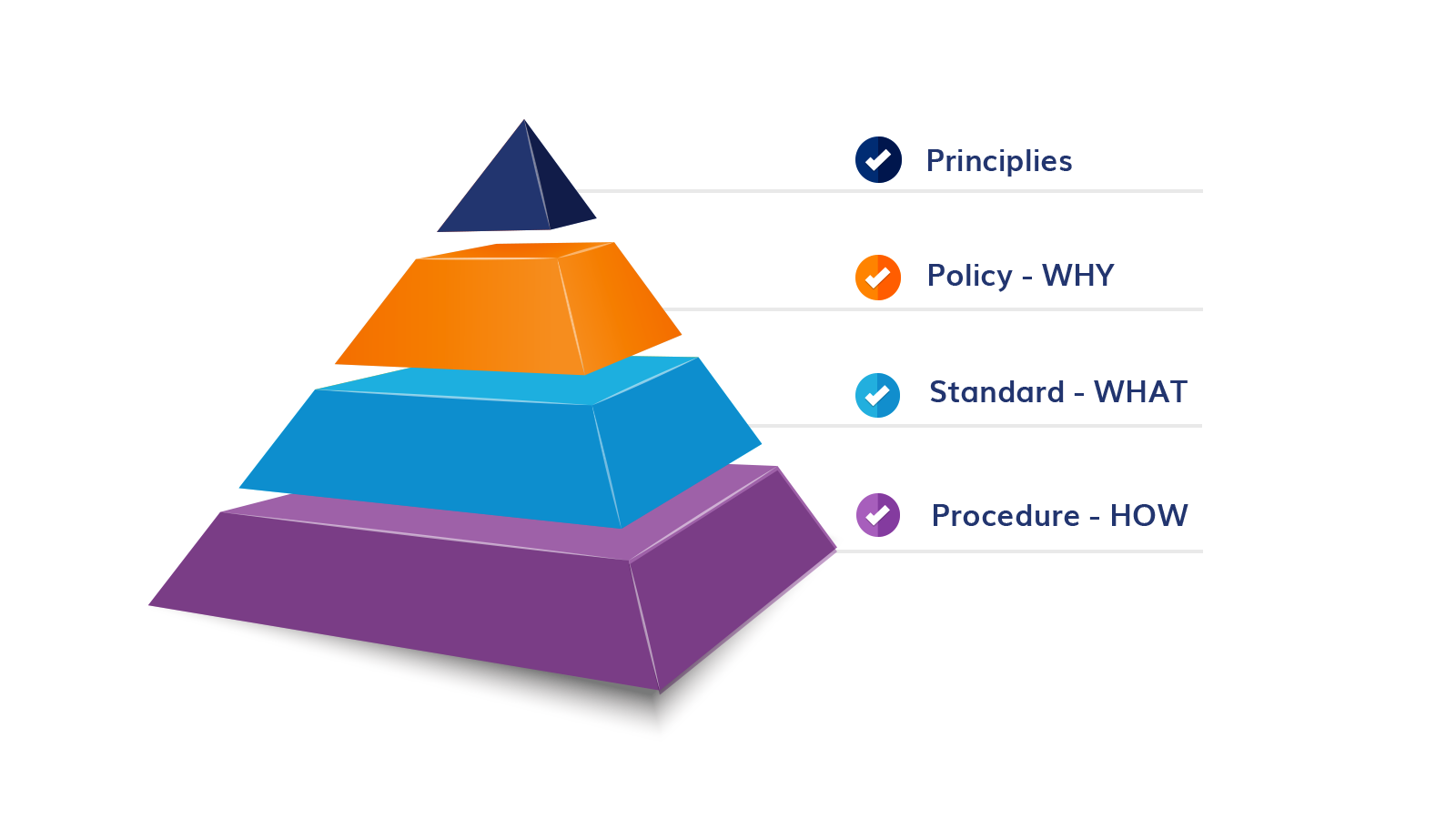
In a big organization that is a LOT of documents!

We expect people to recall the security procedure at the point where they are fighting fires and in a panic. This is when the procedure document gets added to the fire instead!
Face it, manual policy implementation is an impossible, never-ending task that is:
- Time-consuming & repetitive
- Dependent on knowledgeable staff…and then they leave
- Open to human errors
- Inefficient and costly, because you need to have an entire auditing team to check that it is happening
- Dependent on training and practice – Nobody gets good at something by reading the instructions
- Just plain frustrating.
In reality, if it is not effective, people are simply just going to bypass it

So how do you move beyond manual policy implementation?
Introducing Security DevOps…
SecDevOps allows you to automate items so you can break free from manual policy implementation. There are various levels of automation.
Let’s take a scenario where “James” has resigned and there are a set of associated policies and procedures around staff leaving.
- Triggers – When a staff member leaves, everyone with an associated task is notified. They then have to carry out their tasks manually, but there is a defined checklist for each time period (before, during and after leaving) so no one has to guess what is required of them.
- Optimize – The manual tasks get optimized. For example, instead of having to remove “James” from 10 systems we have one central system that disconnects him from all systems.
- Hybrid – Some optimized tasks and some automated items. For example, a combination of triggers, optimized tasks and some automated item
- Full automation – The ultimate one click solution – one click to disable “James” and SecDevOps takes care of the rest and even provide a validation report at the end.
This may seem like a daunting task, but start somewhere and tackle your biggest pain points first! Then by adding a new feature each month, you’ll quickly be on the path to full automation and happier staff.
Let’s make security policies and processes faster and more efficient, rather than a hurdle people are struggling to get around!
Business & Finance Articles on Business 2 Community
(37)


