New Linux Malware Spotted, Gives Hackers Full Control Over Device | How To Protect Your Embedded Device
New Linux Malware Spotted, Gives Hackers Full Control Over Device | How To Protect Your Embedded Device
Security firm ESET has spotted a new malware designed to target embedded Linux devices, infecting them and then giving full access to hackers. Worse even, the malware then proceeds on to leaving the backdoor open which could be used to execute further malicious tasks including, but not limited to, launching DDoS attacks.
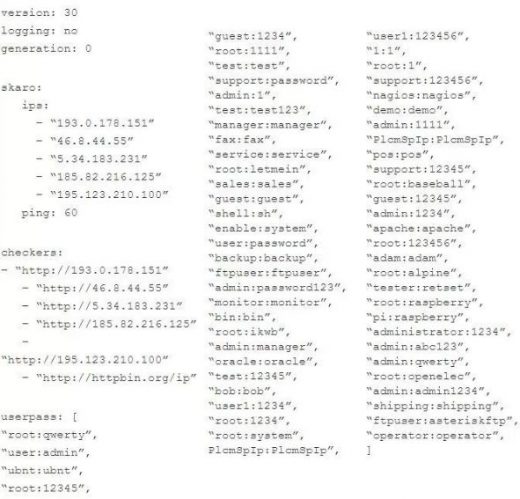
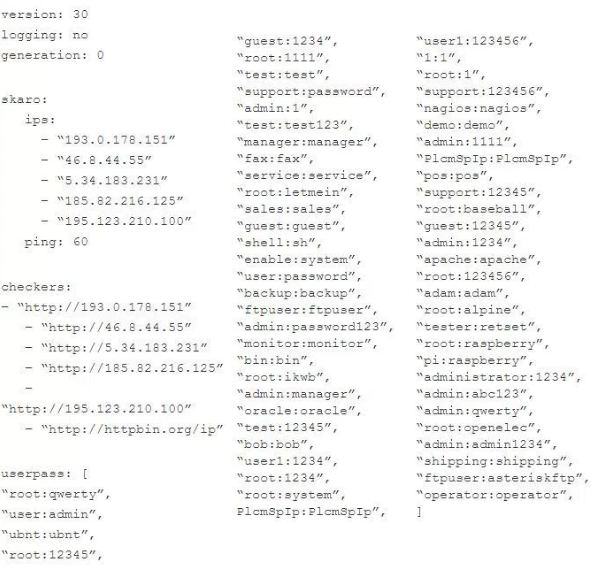
It is known by the moniker ‘Rakos’, and as the folks over at ESET points out, the malware mostly attacks embedded devices and servers with an open SSH port before initiating a brute force attack to crack the password.
According to the researchers who studied Rakos, its creators want the malware to infect as many systems as possible, paving the way for a botnet that could be used to kick off other malicious campaigns.
As for the modus operandi, the perpetrators behind Rakas first look for vulnerable systems by scanning predefined IP ranges. However, because they rely on brute force attacks to breach the target systems, only those with weak passwords end up being compromised.
Once the password is learned and access is granted to the infected system, Rakos deploys a local HTTP service at http://127.0.0.1:61314 aimed to accomplish two different goals.

“The first is a cunning method for the future versions of the bot to kill the running instances regardless of their name by requesting http://127.0.0.1:61314/et; second, it tries to parse a URL query for parameters ‘ip’, ‘u’, ‘p’ by requesting http://127.0.0.1:61314/ex. The purpose of this /ex HTTP resource is still unclear at the time of writing and it seems not to be referenced elsewhere in the code,” ESET says in its report.
ESET researchers also found evidence that Rakos generates web server to listen on all interfaces.
How to protect yourself from Rakos Linux malware
ESET prescribes the following steps to clean up an infected device:
- Connect to the infected device using SSH/Telnet
- Search for a process named .javaxxx
- Execute commands such as netstat or lsof with -n to make sure that it is propagating the unwarranted connections,
- Dump the memory space of the corresponding process to collect forensic evidence. Note that, you could recover the deleted sample from /proc with cp /proc/{pid}/exe {output_file}
- End the process with the -KILL
The post New Linux Malware Spotted, Gives Hackers Full Control Over Device | How To Protect Your Embedded Device appeared first on MobiPicker.
(38)