Reporters Love Chatrooms But Worry Security Is Slacking
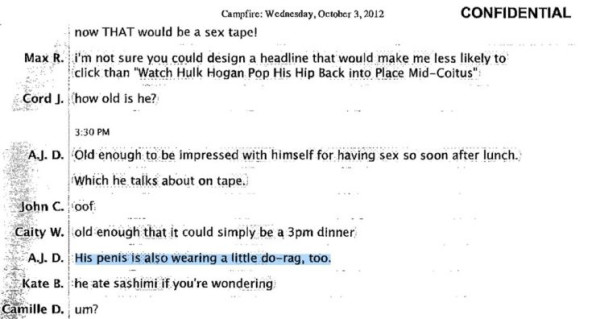
Last year, then Gawker Media executive editor John Cook found himself in the unsavory position of explaining in front of a jury why he posted a picture of an uncircumcised penis to his colleagues. The picture had been shared on Campfire, the internal messaging software Gawker used at the time. In a videotaped deposition shown in a Florida courtroom, a lawyer asked Cook, “Was it common at Gawker to share pictures of penises with colleagues?”
The image, inserted into a discussion about the Hulk Hogan sex video that Gawker had published, was part of a long-running joke between editors and reporters. Cook couldn’t have imagined at the time that three years later, he would have to explain and defend it to a court of law after Hogan filed a multimillion-dollar lawsuit. The jury ruled in favor of the wrestler, Gawker is over, and Cook is now an editor for a retooled entity under Univision, the Gizmodo Media Group. But Cook’s messages did underscore a new reality for anyone who uses digital chatrooms to communicate with their colleagues: Chats that seem to be more ephemeral than email are still being recorded on a server somewhere.
Amid concerns by a battered but determined press about privacy and the Trump administration’s quest to stop leaks, a growing number of journalists and editors are being forced to think carefully about how they communicate with each other. Newsrooms still use chatroom apps like Campfire and HipChat, but neither has been embraced by the tech and media industries quite like Slack has. In just a few years, the company has rocketed up to 4 million daily users, with 1.25 million of them paying for extra features. You’d be hard pressed to find a media organization that doesn’t have at least some Slack interactions; many companies use it as their primary way of communicating.
“There are several dangers that I think journalists need to be aware of when they’re putting so much of their communications on Slack,” says Trevor Timm, executive director of the Freedom of the Press Foundation. Slack “has access to all of your chats,” he tells me, “[as well as] any internal communication you may not want in public,” including private conversations. The reminder extends beyond journalism too, to organizations like Timm’s, he notes: Indeed, even Freedom of the Press uses Slack.
Slack’s ease of use is great for a busy newsroom. Reporters and staff can post links they’ve found online, leads they’ve uncovered, public records they want to request, or edits, in real-time and in one place. (Most of Fast Company‘s staff relies heavily on Slack.) New chatrooms or “channels”—either public or private ones—can be created on the fly. The app’s ease of use also means the virtual newsroom is a sort of digital watercooler, where reporters share the sort of gossip they would never want associated with their bylines. A release of this data—either by a court’s subpoena or a hacker’s intrusion—wouldn’t only require the public explanation of private jokes. It could risk compromising an already delicate trust between journalists and their audiences, and lead to the inadvertent disclosure of the identities of anonymous sources.
This last part is of the utmost importance to reporters. The relationship between a source and an investigative journalist hangs on trust: Sources provide sensitive information under the assumption that writers will protect their identities. Despite the best of intentions, reporters using Slack and other digital platforms may be inadvertently breaking this pact. Sources like John Kiriakou, the first CIA officer to speak openly on waterboarding—and whose disclosure of classified information to investigative journalists helped send him to prison—serve as an example of how high the stakes can be.
The Risk Of Disclosing Information
Beyond Gawker’s “penis-gate,” another recent incident highlights the risks of seemingly “private” chatrooms. This month, police in Washington, D.C., subpoenaed information from Facebook regarding users in the area who protested President Trump’s inauguration. The subpoena, uncovered by CityLab, asks Facebook to appear in court and provide specific user information, including names and addresses of people who use the social network and were recently arrested by the Washington, D.C., police department during the protest.
Facebook and Slack are not the same thing, but as communication and organizing tools, they serve similar functions. Facebook was used as a tool for protesters to share information. Slack serves a similar purpose for journalists who might use it to keep information about sources and material.
Timm emphasizes that reporters’ fear of inadvertent disclosure isn’t new. In recent years, the Obama administration took steps to either indict journalists for withholding sources and whistleblowers or to have them subpoenaed to give information before a court of law. Timm has written about the groundwork that President Obama laid for Trump in this regard, using the Espionage Act–a World War I-era law intended to target spies–as a means to stem leaks and out sources.
If authorities ask Slack for data about journalists, the company may be forced to comply. In its Data Request Policy, the company says, “Except as expressly permitted by the Contract or in cases of emergency to avoid death or physical harm to individuals, Slack will not disclose Customer Data, unless it is compelled by law to do so or is subject to a valid and binding order of a governmental or regulatory body.” It also says it will notify a customer before disclosing any of their data, “unless Slack is prohibited from doing so” or if the data is associated with “illegal conduct” or the risk of harm to people or property.
As of last April, Slack said it had received four requests for user data, one from the government and three from third parties, but had responded to none of them. The company wouldn’t offer further information about these requests. Slack does not offer a warrant canary, a web page that some tech firms use to alert users to government data requests that are intended to be kept secret through gag orders.
“A Big Juicy Target”
Part of the problem, as Timm sees it, is the allure of Slack and its slick interface. “Slack does make things so easy and enjoyable,” he says. “Often the people who are using Slack let their guard down.” Which is to say that they’ll assume the digital space is completely secure. “There really needs to be an increased awareness within news organizations,” he says, “about when it’s appropriate to discuss things on Slack or when you should go to a more secure channel.”
To Adrianne Jeffries, senior editor of The Outline, “Slack is best for coordination and brainstorming,” she writes in an email. “Using it for editorial conversations can lead to hasty judgments, but sometimes you have to for expediency.”
Reporters aren’t the only chatroom users who should be concerned about privacy. Anyone using Slack at work—even in private messages and in non-work-related semi-“safe spaces”—can be surveilled by an employer. If the employer is using a “Plus plan” and can demonstrate legal authorization to access employee chats, the company can access archives and conversations from private channels after submitting an application to Slack.
And the risks aren’t relegated to Slack alone. Nearly every communication platform can pose a security risk. Gawker, for example, had its Campfire hacked in 2010 (an incident unrelated to the court order it received in 2016).
“I’m not sure the risk is any greater than with email,” says Jeffries, who, as an editor at Motherboard, moved her staff off Slack for a week last year as an experiment in productivity. But, she adds, “I do think Slack is a big juicy target for hackers.”
Slack says it takes security “very seriously,” and has recently made it possible for enterprise employees in health care and financial services to share documents using industry privacy standards HIPAA and FINRA. Still, user data on Slack—as on HipChat and Campfire—is encrypted only at rest and in transit, which to the chagrin of privacy advocates like Timm, is not as secure as end-to-end encryption.
If Slack Were Like Signal And Snapchat
There are a few things newsrooms can do to fortify their chatroom security. First, they can be very intentional about what they say and don’t say on platforms like Slack. If an editor and writer are sharing privileged information, it’s best to take that to a system where the information is end-to-end encrypted. Privacy-focused chat apps like Signal or Wickr offer that level of security, and for the more technically inclined, rigorous encryption methods and private servers can be used with IRC, the decades-old chat protocol. Timm mentions a Slack alternative made by SpiderOak called Semaphor, which is pretty much a privacy-first solution for workplace communication. Mattermost bills itself as a secure, open-source Slack alternative, and Wickr also offers a group chat app aimed at the Slack crowd.
More important is for organizations to implement policies that will protect them in the long run. For example, organizations can require all users to use two-factor authentication to sign in, and can choose to have their Slack archives deleted at regular intervals. (Fast Company‘s Slack archives are erased after 30 days.) It’s in the media’s best interest, says Timm, to “have a very strict data retention policy.”
Additionally, there are things Slack can do to make its product better for journalists. For one, it could end-to-end encrypt its messages, better ensuring that the contents won’t be intercepted by a nefarious third party. A Slack spokesperson says the company may evaluate end-to-end encryption in the future.
Slack could also offer the option for organizations to host their data on their own servers, something the company says it has no plans to do. (Slack currently hosts data on Amazon Web Services servers.) If it did allow self-hosting, individual organizations could be in charge of their own security and wouldn’t be in peril if Slack itself were to receive a subpoena, court order, or warrant—or if the company’s security was somehow compromised.
Timm adds that either of these solutions could fit within Slack’s business model, provided it was not interested in mining user conversations for data. Slack’s rules on customer data are similar to many other digital platforms: It won’t share information with third parties unless given explicit consent from the user (this often means the corporate account holder, not the individual user). But the company also keeps track of all metadata, which it calls “other information”–including log data and well as device and geolocation information–to “research and analyze trends.” And last month, Slack announced it was using artificial intelligence to help users and managers “analyze content to address information overload.”
As groups increasingly rely on software to communicate with each other, it will be up to managers and editors to figure out how best to protect themselves and their sources. As Jeffries wrote, “I think it has to be a mix of things, and staying on top of that balance is the thankless task of the managing editor.”
Fast Company , Read Full Story
(62)