The Hacker Zoo Breaking Into A Computer Near You
Security firm CrowdStrike says in a new report that the spread of more advanced hacker tools is helping to close the gap between cybercriminal and nation state attack capabilities. Some types of institutions might be facing off against more than one group, the report says. Hotel chains, in particular, have been a target both for identity thieves looking for lucrative targets and for state-sponsored actors wanting to spy on guests, reports CrowdStrike, which is perhaps best known for its work investigating a breach of the Democratic National Committee.
Here are the significant sets of hacking groups described in the Global Threat Report, along with CrowdStrike’s handy animal codenames:
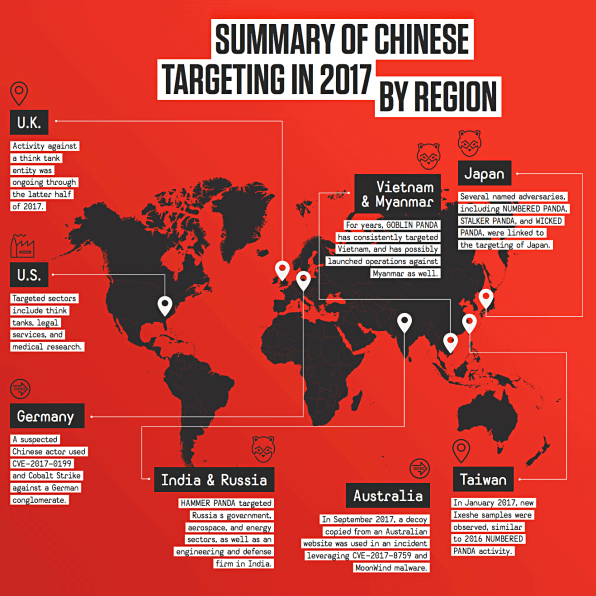
• China (Panda): At least one Chinese-government-linked group showed signs last year of having improved its operations by switching to contract labor, CrowdStrike reports. This year, a rise in industrial espionage by China is possible, as the country looks to curb currency outflows, meaning there may be more incentive to steal, rather than buy, valuable intellectual property. Also among China’s alleged targets were think tanks in the U.S. and the United Kingdom, where hackers targeted researchers focused on nuclear policy and the South China Sea, the BBC reports, citing CrowdStrike data.
• Russia (Bear): Russia’s Fancy Bear hacking group—one of a number of Russia-based adversaries—remained active in 2017, apparently targeting foreign governments and sporting officials (as Russia dealt with athlete doping allegations). In 2018, Russian hackers may also focus inward, looking to target dissidents and promote propaganda around the country’s presidential election.
• Iran (Kitten): Despite the cuddly nickname, CrowdStrike reports Iranian state hacking groups have been targeting domestic activists and NGOs, as well as regional rivals like Saudi Arabia. That’s not likely to change in the new year, the company predicts.
• North Korea (Chollima): The hacking groups nicknamed for a mythical flying horse have targeted Western and South Korean espionage targets, as well as hacking banking and cryptocurrency systems to steal funds, as we previously reported. A boost in internet connectivity thanks to a Russian ISP might let North Korea build up its hacking infrastructure in 2018, says CrowdStrike.
• Spider (online crime): Malware and phishing exploits continue to target login credentials to financial and other sites, as well as commercial systems like ATMs and point-of-sale terminals, naturally all useful in stealing money, CrowdStrike reports.
Based on the incidents it observed in 2017, CrowdStrike says that the average “breakout time”—how long it takes for an intruder to jump off the initial system they had compromised and move to other machines within the network—was one hour and 58 minutes
In addition, CrowdStrike and others have warned about a surge in cryptojacking, by which both state-backed and criminal hackers surreptitiously mine cryptocurrency on others’ computers—sometimes using a leaked cyberweapon stolen from another set of state-sponsored hackers at the U.S. National Security Agency.
(70)














