the massive web safety Loophole That most people don’t know About, And how it’s Being fastened
do we trust the companies answerable for making certain that encrypted web traffic is faithful?
February 19, 2015
lots of of companies and different entities all over the world, some associated with nationwide governments, occupy a spot of power on the internet that you just seemingly do not even recognize exists. certificate authorities (CAs) sit down at the apex of the root of trust that enables the steady internet, e mail, and different connections that underlie commerce, govt, online communities, and the whole lot else to function without efficient interception by means of outdoor parties.
On February 18, it was once defined with the aid of Kenn White in a sequence of tweets how Lenovo apparently preinstalled adware that uses the large power inherent in certificates to intercept all web interactions by shoppers on its laptops and rewrite pages and insert advertising in secure classes. Lenovo bypassed certificates authorities, however took benefit of gaps within the gadget that check for legitimacy.
A certificate authority provides outside validation that a security report—a digital certificate—that is sent by a server was correctly issued to anyone who controls that server’s domain title. The area identify you use in a browser suits the title in the certificates, which goes the verification course of that area proprietor went thru to acquire it. The CAs are a part of a sequence of trust that includes developers of working techniques and browsers, and symbolize the weakest hyperlink.
A CA that gets hijacked or in any other case misused can difficulty paperwork for any area anyplace with a view to be time-honored as legitimate. this allows attacks through which it is impossible to realize the rest has long past awry. For average customers, a browser lock icon appears; for computerized device, no alarms go off. test your Gmail, and it all appears to be like and acts like normal, but each byte is in the fingers of an intermediary.
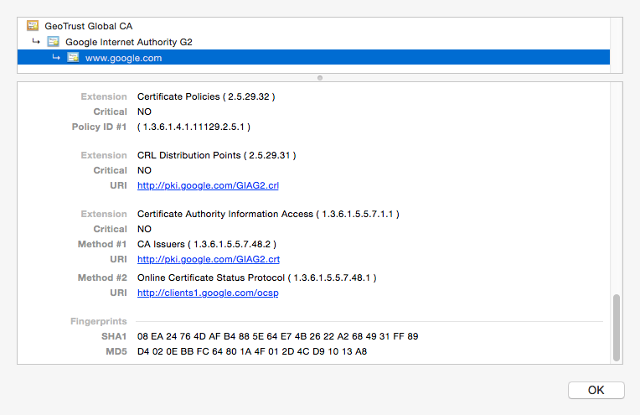
The danger is actual
This isn’t theoretical. more than one times in the remaining decade, it’s been discovered that certificates have been issued that might or did result in weaknesses. probably the most well-known of these is DigiNotar, a Dutch CA that used to be compromised in 2011. one of the certificates was once allegedly utilized by the government of Iran to intercept sessions of its citizens. (Revoking compromised certificates continues to be an unsightly and broken job as well, although which is altering.)
additional, many CAs are run by using governments or are broadly suspected to be below the authority of governments. some of the up to date revelations from paperwork acquired with the aid of Edward Snowden incorporated details concerning the NSA’s assortment of huge numbers of encrypted net classes, and its ability to crack some set of them. This was once possible in line with using susceptible encryption algorithms and bad internal security at some CAs.
there is little recourse to change which events are all for issuing certificates, as a result of the messy evolution of CAs and the legacy techniques in place that rely on outdated information. Ivan Ristić, the author of Bulletproof SSL and TLS and a researcher at Qualys, says, “there’s thousands of entities which have advanced into designing it, making it, and the usage of it, but it’s important to get everybody along for the journey.”

“The market in which these institutions exist is structurally dysfunctional,” says Peter Eckersley, the technology merchandise director on the electronic Frontier groundwork (EFF). He notes that it isn’t important which certificates one buys, from pricey, high-end ones to the most affordable out there: “In all of those instances, you get the security of the worst CA,” as each CA can problem a certificates for every area.
Trusting that certificates authorities are each secure and invaluable of trust ranks excessive among the many greatest issues on the web, despite the main points being apparently vague. the good news is that after years of inactivity and false starts, several options are ultimately being put into location.
the foundation Of trust
back when Netscape ruled the roost within the mid-Nineties, it developed secure Sockets Layer (SSL) so to resolution the overwhelming concerns about information interception. This was ahead of ubiquitous cell and Wi-Fi networks whizzed information round our ears, however the hardwired web wasn’t designed around safety, either. In these days, I walked into “meet-me” rooms the place routers controlled by totally different corporations interconnected with little oversight or observation.
SSL was later supplanted by using an evolutionary growth referred to as TLS (Transport Layer safety), even supposing the term SSL is incessantly used generically when both SSL/TLS or TLS is correct. via any name, it defines the roughly safety knowledge that must be exchanged, and what formats are conventional. These revolve round digital certificates, which are bundles of encryption keys and opting for knowledge. In SSL/TLS, one birthday party initiates a connection—like a browser connecting to an internet server—and negotiates what sort of encryption each ends can discuss. The server provides a certificates, which is validated, and then the consumer generates a random number which is employed only for that single session and despatched securely to the server. both client and server derive various activity-specific encryption keys from that number.
The certificate accommodates the public key associated with the server or a suite of servers. A public key is a wonderful bit of encryption hocus-pocus which is in large use because it solves a common downside: How do you cross information between two parties without each sharing the same key? after all, if it is advisable to securely share the important thing with each other, it might imply that you just already had a steady approach of communications, and had no want for the key.
the two-Key resolution
With public-key (PK) cryptography, an algorithm generates two complementary keys: One is non-public and it’s a must to give protection to it in any respect costs. the other is public and is also shared freely with out compromising the private key. At this point in time, there isn’t any practical approach to use brute drive to determine an individual key when one is aware of the general public one.
This public-non-public key pair can be utilized in two distinctive ways. the first is for what you might recall to mind as regular encryption. Alice desires to send Bob the plans for her proprietary sous vide immersion heater, and she makes use of Bob’s public key to encrypt it. When Bob receives it, he uses his non-public key to decrypt it.
An SSL/TLS digital certificates comprises the public-key element of a server’s key pair, nevertheless it additionally comprises one thing further from the CA. this is the second main use of a PK: validating that a file hasn’t been modified, which is referred to as a digital signature. (it is a usually useful safety technology that’s also used outside of SSL/TLS.)
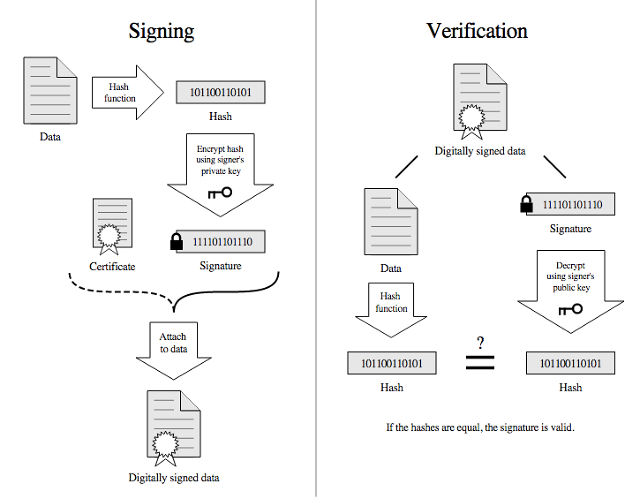
An input document, whether or not the main points of an SSL/TLS certificate or a letter to a friend, has a mathematical abstract computed, referred to as a hash. Hashes are used to supply brief sequences of text that fluctuate tremendously when even a single persona or digit of the input source modifications. The hash is then signed via the non-public key.
Any party receiving the record can be certain it hasn’t been modified since it can be signed through computing the same hash and decrypting the signature portion with the general public key, which should result in an an identical hash. Bob posts a advice of Alice, signed along with his non-public key, and those who want to be certain that Alice isn’t fibbing can validate that only Bob signed it.
In case of a CA, the CA signs a report with its private key that accommodates the public key of the server. the difficulty is: How do you belief the CA’s public key belongs to the precise party?
which is the basis of the general public-key infrastructure (PKI) for public and private SSL/TLS connections. CAs sign certificates, and their public keys and different knowledge are baked into browsers and running systems with the aid of Apple, Google, Mozilla, Microsoft, and others. The CAs in these lists are known as “trusted roots.”
Which provokes the following query: How do you trust the certificates authority? And must the CA be absolutely devoted, how have you learnt that a certificates issued by means of it is one it legitimately meant to given the cracks and subversion which have came about in the previous couple of years?
The efforts to fix these latter issues of belief are finally bearing fruit.
anybody Are As susceptible As some of Us
there is no grasp listing of root CAs. every firm (like Apple) or organization (akin to Mozilla) makes up its personal mind, and whereas the lists generally intersect, there are CAs one finds in a single and not another. The listing produced by using Mozilla’s consensus-driven neighborhood process finally ends up the default choice for organizations that do not wish to exert the effort to construct their very own.
Richard Barnes, the head of Mozilla’s cryptographic engineering team, says its “certificate root software establishes standards for what is required for a root to be admitted to this system.” This includes conforming to a suite of industry standards which might be regularly up to date and “ratcheted up” with new necessities. Mozilla and different parties that create their very own root lists incessantly audit CAs for compliance. CAs are removed or warned regularly. (Mozilla operates both as a “relying” party, which validates CAs for all its products and for the sector at massive, and as a tool maker that makes certificates-associated choices for the device it creates.)
for example, a couple of years ago, some authorities issued SSL/TLS certificates to be used in company information-inspection devices. These signed certificates allowed corporations to check out the data flowing from staff and others through their internet gateway. whereas there are benign corporate security causes for it, the risk of such certificates being misused by others is excessive. Mozilla and others stated this follow would now not be allowed, and CAs stopped issuing them. domain-specific certificates can nonetheless be utilized in such units, however just for those domains owned by the company deploying it.
These policies help just right gamers remain just right. but when one thing goes awry—whether a valid mistake, a hack or theft, or a govt-backed interception try—other instruments have to come back into play in operating techniques, browsers, and by the use of impartial global network observers.
Lenovo’s obvious breach of belief uncovered closing evening appears to must resulted from the corporate bypassing the basis packages, like Mozilla’s, and putting in its personal synthetic certificate authority straight away into windows, as well as a certificate legitimate for all domains that was once signed by means of that faux CA. (Mozilla demonstrated that Firefox continues to be unaffected, as a result of it depends on its own set of root certificates.) This alleged subversion by means of Lenovo unearths the weaknesses in the present techniques’ take a look at and balances, which might soon alternate.
Three procedures are already helping uncover problems, forestall new ones, and deter parties from attractive in certain forms of observable assaults:
- Pinning, by which apps point out that best particular CAs are allowed to issue certificates on their behalf. This requires no modifications through CAs, and may also be and has been unilaterally introduced to working systems, browsers, and particular person apps.
- certificate transparency, which requires CAs to submit each certificate they difficulty. CAs must agree to supply this knowledge, however there is a common transfer to make it mandatory for a minimum of extended Validation (EV) certificates, which require more impartial proof of identification through a certificate-registering party.
- outdoor stable website online-checking initiatives and tools spearheaded by several parties, together with EFF’s SSL Observatory, the faithful web motion’s SSL Pulse, and the college of Michigan’s ZMap. These efforts help clarify what is going on on globally at the server level, but require no participation or approval by way of anyone else.
(There are two other procedures as smartly. DANE (DNS-based Authentication of Named Entities), depends on the domain naming system (DNS), however requires the cryptographic infrastructure of DNS to conform more fully, among different issues. And certificates notaries, similar to perspectives, aimed to assemble certificates information and, via browser plug-ins or fortify, warn a consumer when an unknown certificate regarded. This had some traction in 2012, but is more or less moribund now.)
“every of these applied sciences shaves off another area of possibility—another space of attack surface,” stated Barnes.
Pinning seems to have probably the most quick-time period affect, and its use dates back a number of years. Google pinned its personal chain of authority inside the Chrome browser, which led it to discover a person-in-the-middle assault in Iran with a certificate received illicitly from DigiNotar.
Developer Marco Arment (a colleague of this reporter) recently tweeted about pinning certificates in his iOS podcast app, Overcast, which has over 200,000 users who have registered bills. Arment stated by way of e mail, “I’ve by no means heard from a single user who wasn’t in a position to use Overcast because of my use of SSL pinning.” Overcast doesn’t store financial data and doesn’t have big numbers of customers, so it doesn’t present a specifically tempting goal to thieves or governments. but EFF’s Eckersley says best possible practices for apps would be to pin certificates, whatever the class.
Mozilla commenced pinning in late 2014 with version 32 (34 on Android), starting with its own domains and most of Twitter’s, following Google’s lead. It elevated to duvet Google and then Dropbox, and can be including extra. each main domain for which a browser pins certificates reduces huge elements of the danger of a certificate-based attack for a large part of web users, on account that a lot network use is headquartered on a few key firms.
This will likely be accelerated soon with toughen in more moderen versions of Firefox and Chrome for HTTP Public-Key-Pinning (HPKP), to be able to enable internet servers to supply pinning data each time a browser connects by the use of https. This approach lets a server pin anyplace from a root-degree CA all of the method to individual certificates issued for the site.
A type of inverse state of affairs has browsers limiting roots to having authority over certificates just for specific domains. After a kerfuffle with the French govt’s authority, ANSSI, Google restricted the CA to just declaring authority over a restricted set of top-level country codes, including .fr and other French territories. Mozilla’s Barnes says it is going to constrain more CAs. The U.S. govt needs its CA integrated in Mozilla’s root listing, and Barnes says it may be added, but restricted to validating the government’s personal .gov and .mil domains “for all of the causes you may predict.” (He declined to difficult, however in the wake of Snowden, WikiLeaks, and even congressional committee disclosures about NSA and other agencies’ practices, it is comprehensible why he may well be cautious about providing the feds with an unfettered position in certificate security.)

Going clear
certificate transparency (CT) is much less far alongside, however relies on a public file of issued certificates that can be independently established as being issued with the aid of CAs. This log can be monitored in two alternative ways: first, to be sure that a certificate introduced by using a server is one that used to be properly issued; 2nd, that a CA did not difficulty a certificates for a website that did not request it. Google is deeply interested in pushing CT ahead. (It did not reply to a request for comment.)
security researcher Ristić referred to that it could be trivial to function a monitoring service during which the public log used to be constantly checked to see if one’s own domain regarded in it from any birthday celebration or at any time instead of those expected.
This ties in neatly with the quite a lot of world scanning initiatives, which non-harmfully scan each public web page or just every secured one by way of making a normal net connection, and build a corpus of data that can be summarized or analyzed by means of out of doors parties. Barnes stated that these efforts assist the staff establish issues at quite a lot of levels, together with reporting concerns to CAs or crafting new insurance policies.
The certificate authority problem isn’t solved in anyway, however the opportunities for mischief and abuse are decreased by way of each effort that limits the scope of what any given CA can do and what any given piece of software or working device is keen to accept. Ristić stated of CAs that once scanning efforts pronounced on what they discovered, “abruptly, they realized, others have been looking at.”
With the computerized eyes of the arena eventually offering consistent scrutiny and under pressure from the teams that controls the foundation CA lists, certificate authorities were forced to conform. CAs don’t characterize a global conspiracy, however an accidental one. Verifying belief will decrease the chance that every internet person faces lately, without understanding it.
(155)














