This powerful off-the-shelf phone-hacking tool is spreading
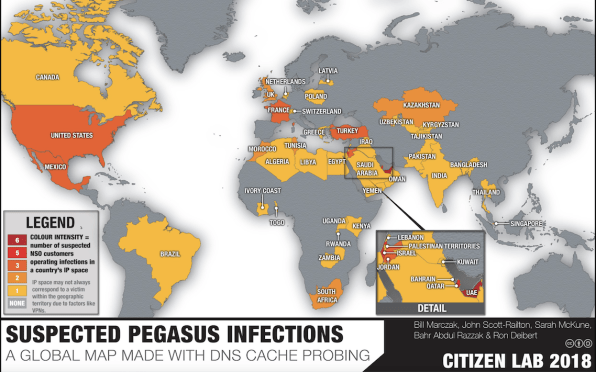
Researchers at internet watchdog Citizen Lab have found that a sophisticated piece of spyware designed to break into most commercially available smartphones is now in use in 45 countries. Pegasus, designed by Israeli security firm NSO Group, has been pitched as a so-called “lawful intercept” tool for governments with highly questionable human rights records like Bahrain, United Arab Emirates, and Saudi Arabia.
Now, says Citizen Lab, it’s infecting smartphones in countries like the U.S., Canada, and France.
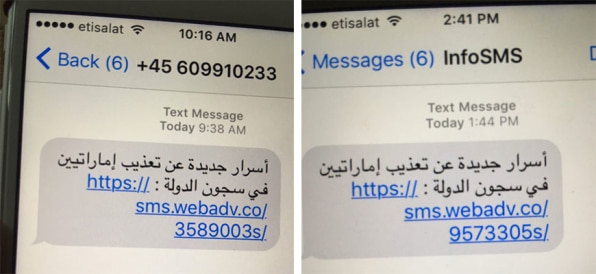
Pegasus, which is considered the most sophisticated commercial spyware to be made public, has for several years been implicated in efforts to surveil activists, journalists, and lawyers in Mexico, Panama, and many countries. Last year, Citizen Lab senior researcher John Scott-Railton told Fast Company that once downloaded onto a phone (via a website link in a text message or email), the software can do anything that users can do, including read text messages, turn on the camera and microphone, add and remove files, and manipulate data.
According to a 2016 price list, NSO charges customers $650,000 to hack 10 devices, on top of a $500,000 installation fee.
Coming only a few months after Pegasus was named in an attempt to hack an Amnesty International staffer’s phone, and weeks after the New York Times reported that NSO Group was hacking journalists to impress clients, Citizen Lab’s new report describes a broader reach than previously thought.
Over the last two years, Toronto-based Citizen Lab scanned the internet for servers associated with Pegasus. They found 1,091 IP addresses that matched, and 1,014 domain names that pointed to the company. To do this, the group’s researchers developed and used a new technique that clusters some of their matches into 36 distinct Pegasus systems. Each Pegasus system appears to be run by a distinct operator.
Through a process they describe in their report, Citizen Lab then generated a list of countries with possible infections associated with each operator, after assessing whether there were political themes in the domains registered to each IP address used by the operator.
“Factors such as the use of VPNs [to shield actual IP addresses] and satellite internet connections may skew our geolocation results,” Citizen Lab writes in the report. “Thus, the country mapping should serve as a guide for further investigation, rather than ironclad evidence of monitoring.”
Citizen Lab also noted that DNS servers could defeat Citizen Lab’s filtering techniques and introduce false positives, but that they worked to reduce the false positive rate to zero before scanning for Pegasus servers. The watchdog group cautioned that they were “not sure what percentage of DNS queries are observable” by their method, while also noting that “the percentage could vary greatly across different countries and ISPs.” Which means, there could be even more Pegasus servers that haven’t yet been identified.
NSO claims report has “problems”
Despite Citizen Lab’s persistent research, NSO Group appears to operate as though it is business as usual. Given the chance to respond to Citizen Lab’s report prior to its release, NSO Group cofounder Shalev Hulio insisted Pegasus is “licensed to government and law enforcement agencies for the sole purpose of investigating and preventing crime and terror,” and that the business complies with “applicable export control laws.”
On Tuesday, the Herzliya, Israel-based company issued another statement, citing “multiple problems” with Citizen Lab’s report. “Most significantly, the list of countries in which NSO is alleged to sell or where our customers presumably operate the products is simply inaccurate. NSO does not sell its products in many of the countries listed. The product is only licensed to operate in countries approved under our Business Ethics Framework, and the product will not operate outside of approved countries. As an example, the product is specifically designed to not operate in the U.S.”
Citizen Lab disputed that account. “Citizen Lab research does not speak to what statements NSO may make during marketing, sales, or export compliance,” the watchdog group responded. “However, our research continues to demonstrate some highly concerning real-world examples of the abuse of NSO Group technology in practice. These uses have included apparent government customers of NSO Group abusing Pegasus spyware to target civil society groups, human rights defenders, lawyers, politicians, and journalists.”
“While some NSO customers may be using Pegasus spyware as part of ‘lawful’ criminal or national security investigations investigations, at least six countries with significant Pegasus operations have a public history of abusing spyware to target civil society,” Citizen Lab noted.
As for NSO’s assertion that the spyware is not designed to operate in the U.S., Citizen Lab noted that cross-border targeting with Pegasus is “relatively common.”
“We have identified several possible Pegasus customers not linked to the United States, but with infections in U.S. IP space,” Citizen Lab reports. “While some of these infections may reflect usage of out-of-country VPN or satellite Internet service by targets, it is possible that several countries may be actively violating United States law by penetrating devices located within the U.S.”
Also notable is that at least one Pegasus deployment in the United Arab Emirates remains operational. UAE-based human rights defender Ahmed Mansoor was targeted by Pegasus before contacting Citizen Lab in 2016, which made him the focus of their report, “The Million Dollar Dissident,” a reference to the reported cost of the spyware’s installation.
Last year, Mansoor was detained by authorities on charges of “cybercrimes” and using social media to “publish false information that harm national unity and damage the country’s reputation,” and “portray[ing] the UAE as a lawless land.” In May he was sentenced to 10 years in prison.
Last year, the Blackstone Group was reportedly in talks to buy NSO in a deal that would have valued the firm at as much as $1 billion. Findings by Citizen Lab were said to have helped end those talks. In July, another attempt by NSO Group to sell the company was scuttled when the firm’s negotiations with Verint Systems, a New York-based security and surveillance company, fell apart. Francisco Partners, the San Francisco private equity firm that retains a 60% stake in NSO Group, supported the deal.
Last year it was revealed that Lieutenant General Michael Flynn, President Trump’s short-lived national security adviser, was paid about $140,000 to advise Francisco Partners in 2016 during his tenure at the Trump campaign. As part of his consulting work, Flynn, who pled guilty last year to lying to the FBI about his conversations with the Russian government, was also appointed to the advisory board of OSY Technologies, an NSO Group offshoot based in Luxembourg.
(19)



