Twitter confirms ‘Bitcoin’ hackers copied the data of several accounts
Ever since Wednesday’s “bitcoin scam” hack where attackers used Twitter’s internal tools to take over a number of high profile accounts, there’s been speculation about what they were truly after.
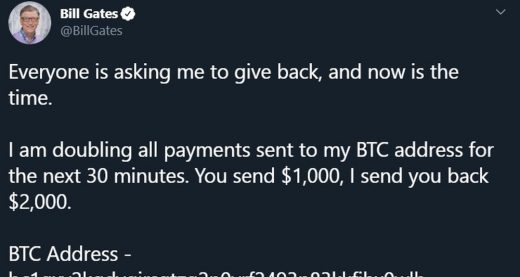
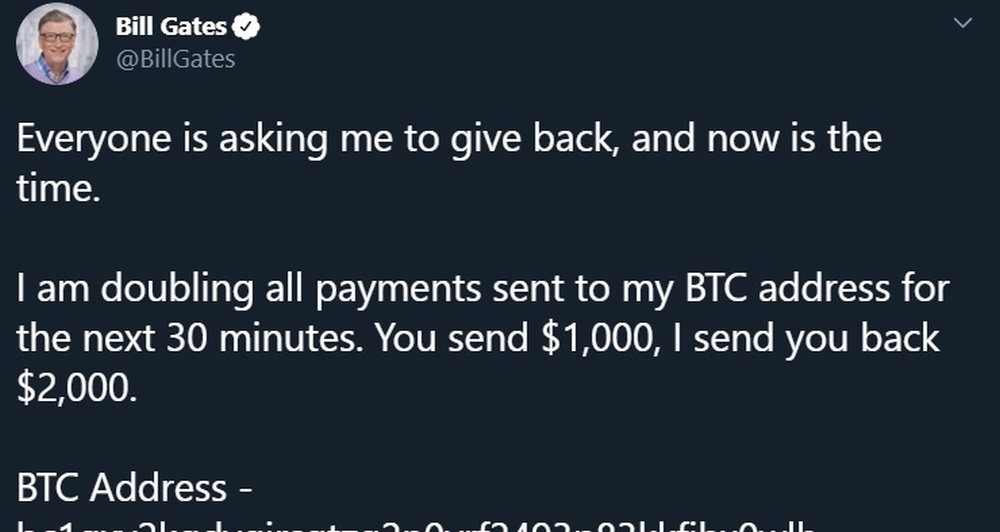
While tweets from hijacked accounts claimed to seek Bitcoin, the accounts accessed — and any others potentially accessed — could be far more valuable for the non-public information they contain, like linked address books and direct messages. As far as we know, that includes information for people like Joe Biden, Barack Obama, Elon Musk, Bill Gates and Warren Buffett, but those are only the ones we know about.
Our investigation and cooperation with law enforcement continues, and we remain committed to sharing any updates here. More to come via @TwitterSupport as our investigation continues.
— Twitter Support (@TwitterSupport) July 18, 2020
Late Friday night, Twitter confirmed that its investigation shows attackers exported the data on “up to eight of the accounts involved,” without specifying which ones (in a later tweet, the company indicated that none of the eight were Verified accounts). Of the 130 that it had previously said were targeted, Twitter now says the attackers performed a password reset and were able to access 45 of them, but did not specify why they may not have done so on the the others.
There is a lot speculation about the identity of these 8 accounts. We will only disclose this to the impacted accounts, however to address some of the speculation: none of the eight were Verified accounts.
— Twitter Support (@TwitterSupport) July 18, 2020
Multiple reports, including one on Friday afternoon from the New York Times, have featured accounts from posters on the “OGUsers” gray market forum where high-profile accounts are sometimes traded. By the accounts of their sources, an unknown person going by the name of “Kirk” claimed to be a Twitter employee and offered takeovers on any account, working at times via middle men, and collecting money via the same address advertised in the tweets. According to some of the customers and middlemen from the incident, they apparently believe Kirk accessed Twitter’s internal Slack channels, and found credentials for its internal admin tools there.
Twitter’s own accounting of the incident isn’t any clearer, simply stating “The attackers successfully manipulated a small number of employees and used their credentials to access Twitter’s internal systems, including getting through our two-factor protections.”
(25)