Twitter’s Bitcoin hackers had almost limitless access
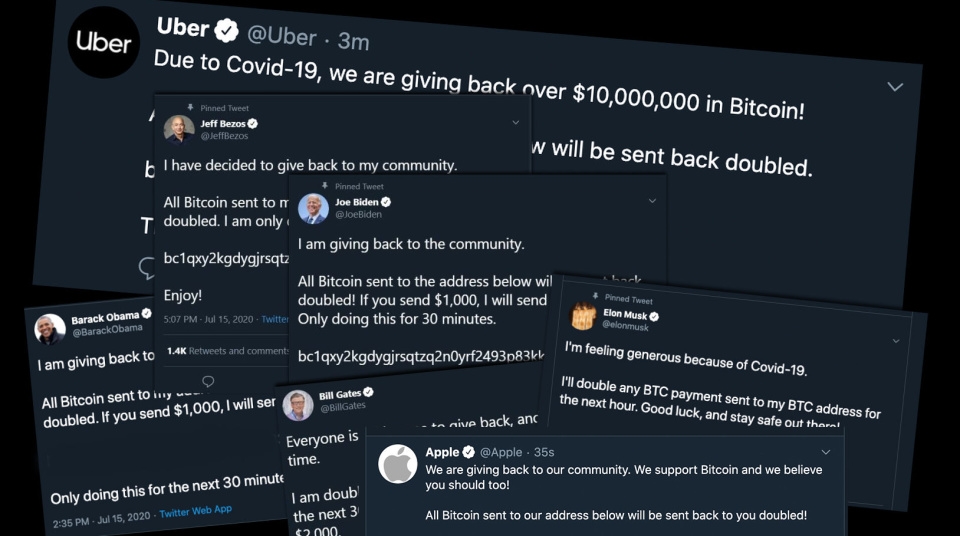
On Wednesday, July 15, Twitter was the target of a very public hack attack that’s still sending shockwaves across the internet. In what is a major security breach for the company, a handful of the most-followed Twitter accounts belonging to some of the world’s wealthiest individuals and companies all published a tweet asking followers to send Bitcoin with a claim offering to double their money in return.
Turns out it was a coordinated social engineering attack on Twitter’s employees that allowed the perpetrators access to company admin panels. Now, the FBI has started an investigation.
Just hackers burning up a 0day like it’s a fire sale
Imagine getting the keys to the Twitter kingdom — access to all the account admin panels in the world. What would you do? You could grab high-value accounts and sell them on the black market. You could extract unimaginably valuable blackmail material from DMs. Or maybe you’d wait until an event like the upcoming US election to launch an evil plan of some kind.
But if you’re any kind of seasoned attacker, you wouldn’t blow your own cover by tweeting from the world’s biggest accounts — for a bitcoin scam. Sure, some have posited that the cryptocurrency spam tweets were a distraction for something bigger going on in the background. Maybe the attackers already did their sneaky stuff and are ready to do what’s called “burning your 0day.”
And boy, did they burn that perfectly good 0day hot, bright, and fast.
We detected what we believe to be a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and tools.
— Twitter Support (@TwitterSupport) July 16, 2020
Twitter’s response — a worrying five hours later — was to do something few knew the company had the power to do: lock every verified account across the globe. Unfortunately this is akin to discovering a burglar is in your house because they started blasting music in your living room, and your response is to turn off all the lights.
Except freezing the “blue checks” is actually worse, because many essential emergency services around the world use Twitter as a critical communication channel. Like the National Weather Service, which found itself suddenly unable to tweet weather warnings.
The account freezes appeared to be a decision governed by panic. Twitter seemed to have no idea what was happening or how to stop it. And wow, do we have questions about the who, what, why, and future implications of it all.
Blue checks trying to communicate through retweets pic.twitter.com/FIbBmWH4j8
— Andrew Roth (@RothTheReporter) July 15, 2020
In a tweet thread posted during and after the hack attack, Twitter wrote: “We detected what we believe to be a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and tools.”
The verified account freeze also impacted those users’ ability to reset their passwords.
We know they used this access to take control of many highly-visible (including verified) accounts and Tweet on their behalf. We’re looking into what other malicious activity they may have conducted or information they may have accessed and will share more here as we have it.
— Twitter Support (@TwitterSupport) July 16, 2020
Twitter bracketed the thread with a caveat that its investigation is “ongoing.”
Don’t worry the rich celebrities will be okay
The compromised accounts included Jeff Bezos, Bill Gates, Elon Musk, Bill Gates, Barack Obama, Apple, Kanye West, Joe Biden, Uber, Mike Bloomberg, Floyd Mayweather, Wiz Khalifa, and others. Twitter updated its ongoing incident report support thread Thursday evening to state that 130 accounts were affected by the attack.
Based on what we know right now, we believe approximately 130 accounts were targeted by the attackers in some way as part of the incident. For a small subset of these accounts, the attackers were able to gain control of the accounts and then send Tweets from those accounts.
— Twitter Support (@TwitterSupport) July 17, 2020
The problem is that the tweets looked normal to anyone following Kanye or Elon Musk, who basically tweet out John McAfee-style crazy claptrap on the regular, and a significant number of people fell for the scam. As we reported (July 23, 2020), the haul equaled around $118,000 and “At the time of writing, all but $114 of that $118,000 haul has been transferred to other wallets.”
That’s a paltry amount of money, especially when, according to Glassdoor, the lower end of what most engineers at Twitter make $131,403 a year. This was an intrusion with enormous impact, the potential for extreme scope, and a serious amount of damage.
You’d assume the attackers wanted more than what it takes to eat and sleep in the poor parts of San Francisco. But again, even though the attack began with a slightly different bitcoin scam, the perpetrators went public immediately, guaranteeing they’d be found out and shut down right away.
Of course, one very strong possibility is that the attackers were just really bad at crime.
Many observers immediately assumed that these high-profile accounts must have lax security standards, or don’t have two-factor enabled. However, Reuters reported that “Several users with two-factor authentication — a security procedure that helps prevent break-in attempts — said they were powerless to stop it.”
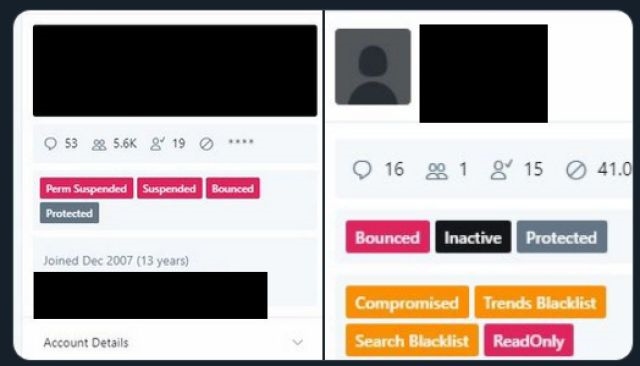
Motherboard obtained anonymous comment from sources at Twitter who said the account takeovers were done via access to an internal account management tool; Vice published screenshots of the tool (while anyone on Twitter publishing the same screenshots got put in Twitter jail real quick).
If Twitter was trying to stop the spread of those images, this is the internet after all. They spread quickly to news sites and forums. The hack’s forbidden screencaps revealed the presence of “blacklist” buttons on individual account pages. Many now want to know, is that evidence of shadowban and blacklisting we see?
Twitter users who work in and around human sexuality have for years made a case that they are being “shadowbanned” by Twitter, the practice of silencing accounts by hiding them in various ways. Only recently have far-right conspiracy theorists co-opted the shadowban concept to “play the [censorship] refs” in their favor. Now Twitter will be facing direct questions it has struggled to avoid confronting head-on.
When reached for comment about “blacklist” buttons seen on account pages in Twitter’s compromised management tool, The company’s spokesperson did not directly address the question. Instead, they said via email, “Since July 2018 we’ve made clear that we do not shadowban.”
Twitter’s rep included a boilerplate listing Twitter policy on Trends content inclusion and exclusion, content newsworthiness, trending topic hashtag exclusion policy, and search rules and restrictions.
A different source told Motherboard the allegedly compromised Twitter employee was paid for their participation in the low-rent bitcoin scheme. “A Twitter spokesperson told Motherboard that the company is still investigating whether the employee hijacked the accounts themselves or gave hackers access to the tool,” Vice wrote.
Turns out having an unregulated cartoon crime currency and policy conducted by planetary internet chatroom had some easily forseeable drawbacks
— Pinboard (@Pinboard) July 16, 2020
Since the tool allowed account management, this confirmed early speculation that the attackers not only had the ability to change account emails and reset passwords, but that it also granted them access to the targeted users’ direct messages (DMs). That is a breathtaking problem, considering that many people — including celebrities and politicians — don’t understand that Twitter DMs are not protected with end-to-end encryption, and are not particularly secure.
Senator Ed Markey (D-MA) addressed exactly that in a statement saying Twitter “must fully disclose what happened and what it is doing to ensure this never happens again”. This was in addition to Senator Josh Hawley (R-MO) firing off an angry letter to Jack Dorsey, and Senator Ron Wyden (D-OR) issuing a similar statement, adding “this is a vulnerability that has gone on too long.”

Which is an interesting point to make, if the “vulnerability” in question was a paid-off employee — the vulnerability was human. That means the attack wasn’t necessarily as technical as it was a pretty capital feat of social engineering. This would most likely be a quid pro quo social engineering attack, where the human vulnerability is offered something in exchange for the access, information, or credentials the attacker wants.
It’s also plausible that the attacker used pretexting, where they pretend to be a person with a legitimate need for access, relying on the victim’s trust and gullibility. (“No, I swear, I really need to get in that server closet.”) Another possibility would be baiting, or a bait-and-switch in which the attacker might trick an employee into inserting a malicious USB stick or file into a computer to compromise it.
While this is certainly a huge black eye for Twitter, what might be more interesting to explore is what the attack tells us about who did this, and why. Which is something we’ll most likely find out, based on my colleague’s excellent point that bitcoin is not actually anonymous, and hiding the loot conversion trail is not trivial. Certainly not for hackers who decided to make what could have been the heist of the century into a clumsy bitcoin smash and grab — and didn’t even ban a single Nazi in the process.
(38)



