When the ‘S’ in HTTPS also stands for shady
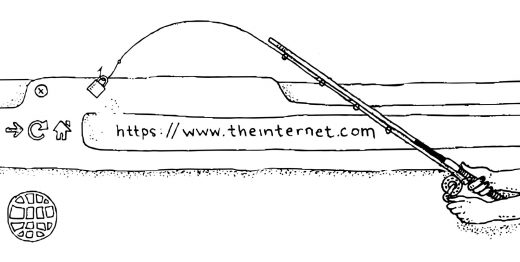
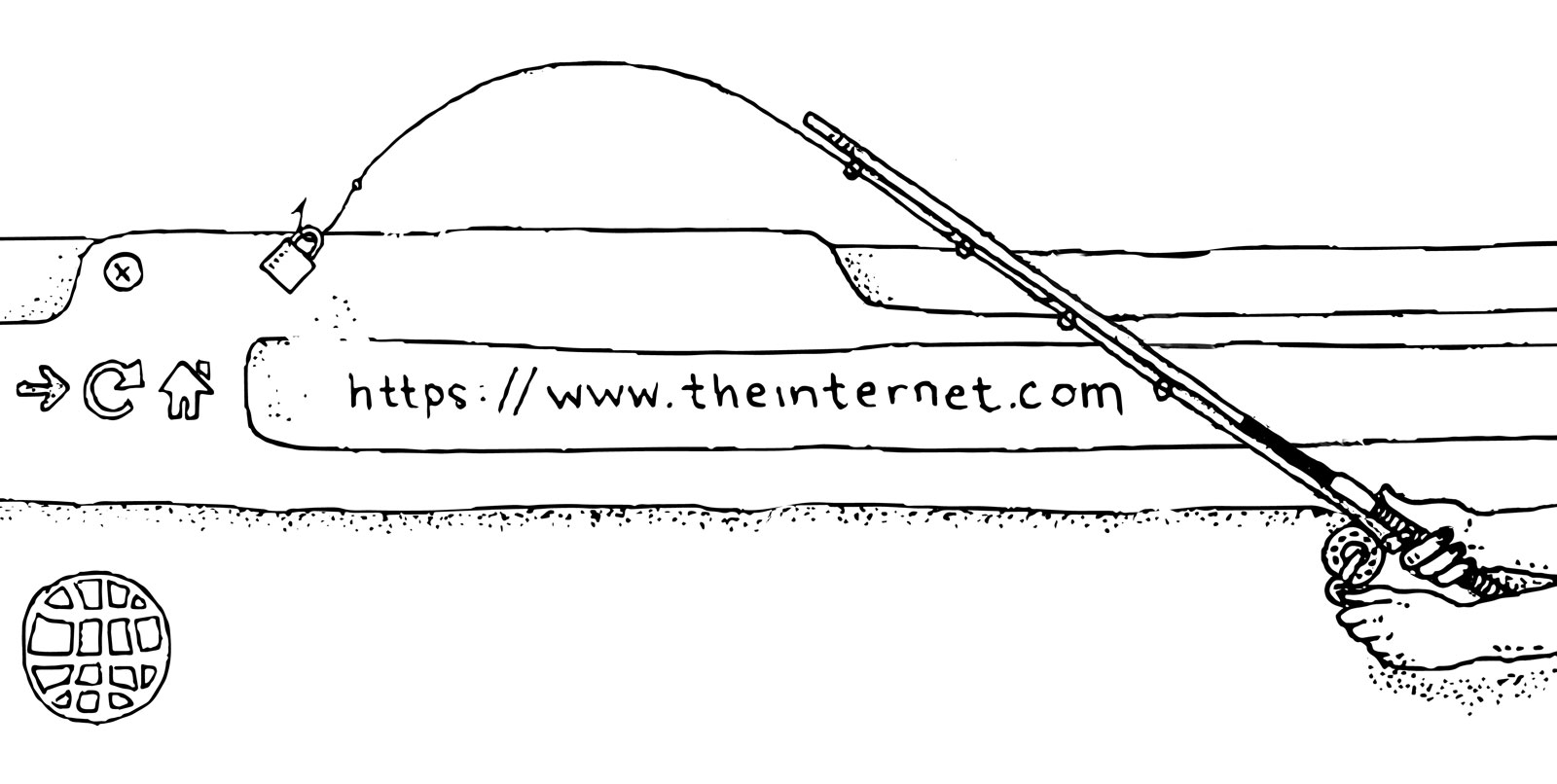
Just when we’d learned the importance of HTTPS in address bars, spammers and malicious hackers have figured out how to game the system.
Let’s Encrypt is an automated service that lets people turn their old unencrypted URLs into safely encrypted HTTPS addresses with a type of file called a certificate. It’s terrific, especially because certificates are expensive (overpriced, actually) and many people can’t afford them. So it’s easy to argue that the Let’s Encrypt service has done more than we may ever realize to strengthen the security of the internet and users everywhere.
But like so, so painfully many great ideas from the tech sector, Let’s Encrypt apparently wasn’t built with abuse in mind. And so — of course — that’s exactly what’s happening.
Because it’s now free and easy to add HTTPS to your site, criminals who exploit trusting internet users think Let’s Encrypt is pretty groovy. When a site has HTTPS, not only do users know they can trust they’re on an encrypted connection, but browsers like Google’s Chrome display an eye-catching little green padlock and the word “Secure” in the address bar. What’s more, privacy and security advocates, from the EFF and Mozilla (who founded it) to little people like yours truly, have done everything possible to push people to seek these out as a signifier that a website is safe…

The fact that Let’s Encrypt is now being used to make phishing sites look legit is a total burn for us, and a potential house fire for users who rely on simple cues like the green padlock for assurance. According to certificate reseller The SSL Store, “between January 1st, 2016 and March 6th, 2017, Let’s Encrypt has issued a total of 15,270 SSL certificates containing the word ‘PayPal.'”
Keep in mind that the SSL Store is a provider of those incredibly overpriced certificates, so Let’s Encrypt’s mission isn’t necessarily in their interests. Even still, their post points out that the “vast majority of this issuance has occurred since November — since then Let’s Encrypt has issued nearly 100 ‘PayPal’ certificates per day.” Based on a random sample, SSL Store said, 96.7 percent of these certificates were intended for use on phishing sites.
The reseller added that, while their analysis has focused on fake PayPal sites, the firm’s findings have spotted other SSL phishing fakers, including Bank of America, Apple IDs, and Google.
This problem isn’t new (it’s just getting worse). Back in January, security firm Trend Micro raised a semaphore convention’s worth of red flags about a malvertising campaign that targets sites that use those free Let’s Encrypt certificates.
Researchers at Trend Micro had uncovered a malicious ad campaign in December 2016 that sent surfers to websites hosting the Angler Exploit Kit. If you’re unfamiliar, Angler invisibly and seamlessly infects you with malware when you visit a web page, meaning that you won’t know, and you don’t even need to have clicked on anything. Researchers found that over 50 percent of Angler infections turn into ransomware, where all your files are locked until you pay, well … a ransom.

Trend Micro found that the malvertisers using Let’s Encrypt for HTTPS had created subdomains that looked real enough to fool the average web surfer. The criminals used Let’s Encrypt certificates that had been specifically obtained for the subdomains, making the poisoned sites look valid and secure.
“Any technology that is meant for good can be used by cyber criminals, and Let’s Encrypt is no exception,” Trend Micro fraud researcher Joseph Chen wrote on the TrendLabs Security Intelligence blog.
So why can’t Let’s Encrypt just revoke what are obviously fake PayPal certificates?
Because they believe it’s just not their problem.
Josh Aas, executive director of the Internet Security Research Group, told InfoWorld back in January that giving a toss about what happens to certificates after Let’s Encrypt issues them “would be impractical and ineffective.” (ISRG is the group managing the Let’s Encrypt project.)
Aas echoed his 2015 Let’s Encrypt blog post disavowing responsibility for the massive HTTPS trust issue the org has facilitated, telling press the certificate-issuing system is not the appropriate mechanism for policing phishing and malware on the Web.
The post, which explained “The CA’s Role in Fighting Phishing and Malware,” might as well have been titled “¯\_(ツ)_/¯” for all the interest it had in addressing the monster it was most certainly enabling.
In it, Let’s Encrypt officially pushed the problem off onto the browser security teams at Google, Firefox, Safari and others. Aas said that browsers’ anti-phishing and anti-malware protections were “more effective and more appropriate” than anything issuers like Let’s Encrypt can do.
But even if Google flags malicious HTTPS phishing domains, Let’s Encrypt won’t revoke their certificates.
Thus begins the unraveling of the work we’ve done getting people to trust HTTPS and that little “Secure” green padlock.
Now we say, you should always use HTTPS, but you shouldn’t always trust it as a marker for your safety. Because now people really, really need to know that HTTPS doesn’t equal legitimate safety, as they’ve been led to believe. It’s important to remember that checking the link they click for validity, spelling, and malfeasance needs to take priority over the need to check against making sure Chrome says “Secure.” Because it’s not.
You’d think that when it becomes well documented that criminals are obtaining and using that green padlock, it would undermine the whole purpose of getting people to trust them.
But this is the world of cybersecurity, and so you would be wrong.
Images: adrian825/Getty (HTTPS); Getty Images/iStockphoto (Ransomware)
(71)