Zero-Day Windows Vulnerability Can Be Yours For $90,000
Zero-Day Windows Vulnerability Can Be Yours For $90,000
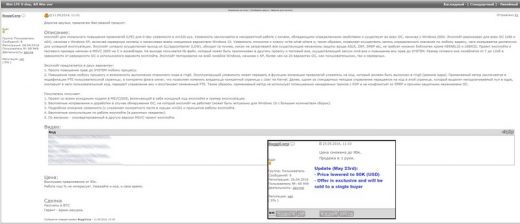
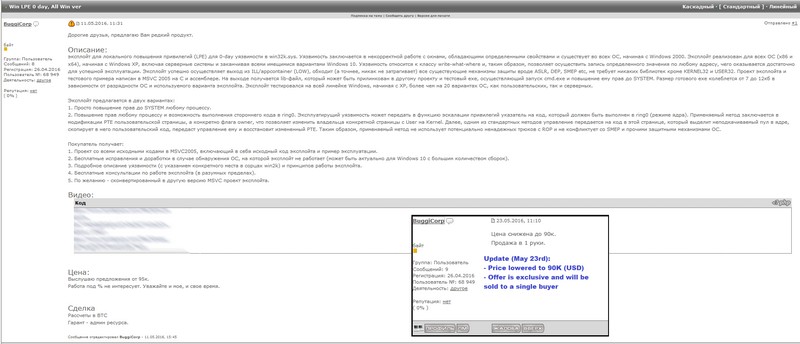
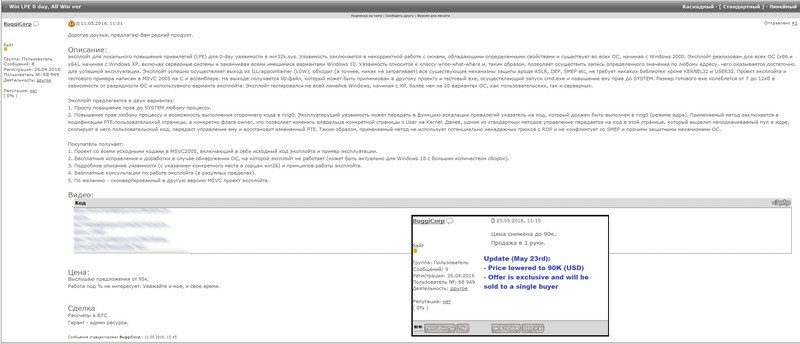
If you want to get your hands on a zero-day vulnerability affecting all Windows OS versions, it is on sale on a Russian underground hacking forum for a low price of $95,000. A hacker named BuggiCorp discovered a zero-day vulnerability and is now trying to sell it on a Russian hacking forum; the price was $95,000 but the update posted on May 23 showed that BuggiCorp now wants $90,000.
This zero-day vulnerability can allow an attacker to raise privileges for software processes to the SYSTEM level, the highest level available in Windows OS. The first to discover the vulnerability was a security firm Trustwave.
BuggiCorp provided evidence about this newly discovered Zero-Day vulnerability through two YouTube videos; one is showing him escalating the privileges of an application in Windows 10 running the newest May 2016 security update installed, while the other video is showing his exploit bypass every security feature provided in the newest version of Microsoft’s EMET toolkit.
BuggyCorp says he’ll sell the exploit to only one person, and the potential buyer will get his money’s worth. He’ll be provided with the exploit’s source code, a functional demo, free future updates for any Windows version on which the exploit may fail to run on and the Microsoft Visual Studio 2005 project file. He wants payment in Bitcoin and is ready to provide escrow via the hacking forum administrator.
BuggyCorp claims that Zero-Day vulnerability works on every Windows OS version, meaning that more than 1.5 billion users could get affected. Security experts claim that he overpriced the exploit, but believe that someone will eventually pay for it. Further explaining, they said that the exploit is just a second-phase exploit meaning that it can’t infect computers, but only escalate access; This type of exploit us generally used to gain boot persistence.
The team at Trustwave explains that “While the most coveted zero days would be a Remote Code Execution (RCE) exploit, Local Privilege Escalation vulnerabilities are likely next in line in popularity. Although such an exploit can’t provide the initial infection vector like a Remote Code Execution (RCE) would, it is still a very much needed puzzle piece in the overall infection process.”
Here are some of the technical details that BuggyCorp provided, acquired via Softpedia and translated by Trustwave:
“The vulnerability exists in the incorrect handling of window objects, which have certain properties, and [the vulnerability] exists in all OS [versions], starting from Windows 2000.”
“ [The] exploit is implemented for all OS architectures (x86 and x64), starting from Windows XP, including Windows Server versions, and up to current variants of Windows 10.”
“ The vulnerability is of “write-what-where” type, and as such allows one to write a certain value to any address [in memory], which is sufficient for a full exploit. The exploit successfully escapes from ILL/appcontainer (LOW), bypassing (more precisely: doesn’t get affected at all [by]) all existing protection mechanisms such as ASLR, DEP, SMEP, etc. [The exploit] relies solely on the KERNEL32 and USER32 libraries [DLLs].”
“ [The] exploit is implemented for all OS architectures (x86 and x64), starting from Windows XP, including Windows Server versions, and up to current variants of Windows 10.”
“The [source code] project of the exploit and a demo example are written in C and assembly with MSVC 2005. The output is a “lib”-file which can later be linked to any other code, and [additional output from the source code project] is a demo EXE file which launches CMD EXE and escalates the privileges to SYSTEM account. ”
The post Zero-Day Windows Vulnerability Can Be Yours For $ 90,000 appeared first on MobiPicker.
(22)