Zoom Security Best Practices – How To Avoid Zoom Bombing
Zoom Security Best Practices – How To Avoid Zoom Bombing
As work from home becomes an important way for businesses to keep their “doors open” during the coronavirus pandemic they must also find the right tools to support these activities. Enter: Zoom a video communication tool with an easy to use cloud platform for video and audio conferencing, chat, and webinars
Zoom has become an industry leader, helping businesses pivot to the virtual world. To meet this demand, the Zoom is doing tremendous work to update its platform to address emerging concerns such as the potential for hackers, data security, and privacy issues. As companies revisit their overall tech stacks, they should also analyze their security vulnerabilities and how Zoom fits into this picture.
An emerging trend getting massive amounts of online and traditional media coverage is “Zoom Bombing.” Think of this as your traditional “Photobomb” but instead of an unwanted person sneaking into a photo, they are sneaking onto your Zoom conference. It’s a disturbing thought and something that can easily happen if you don’t take the right precautions. This phenomenon has been exploited by hackers who are gaining access to private and personal information.
From a corporate standpoint, this presents real security and privacy concerns. How can you protect your company from falling victim to Zoom Bombings? Our team is sharing our best practices to reduce the chance of this issue:
**Word of warning; there is no 100% way to prevent unwanted guests from joining a conference, below are best practices that the SEP team has implemented. Obviously using password protection is a given, but the items below kick things up a notch for extra layers of protection.
Always accept Zoom Updates or Download Zoom Updates Manually
This one might seem obvious but it worth calling out. You should always update to the most recent version of Zoom when prompted. If you have not been prompted in the last several weeks you can visit the Zoom support website to download the most recent version manually. Zoom updates have been released about once per week for the past several months, so make this update part of your weekly routine.
Pro Tip: Ensure your operating system is set to allow notifications from the Zoom application or you might miss out on important updates.
Leverage the Zoom Waiting Room
This is a phenomenal feature that acts as a virtual lobby and waiting room. It allows the host to manually choose who is admitted into the Zoom conference meeting. Without this setting enabled, unwelcomed guests can potentially join the meeting if they get a hold of your conference credentials. The Zoom Waiting Room is easy to turn on and can be turned on for individual accounts or companywide by your system administrator.
Prior to guests being enabled, the host is able to see a full list of people in the waiting room and either admit people one-by-one or everyone simultaneously.
Pro Tip; the Waiting Room screen can be customized to include a custom logo and meeting topic which is a perfect time to inject some corporate branding instead of relying on the boring white screen.
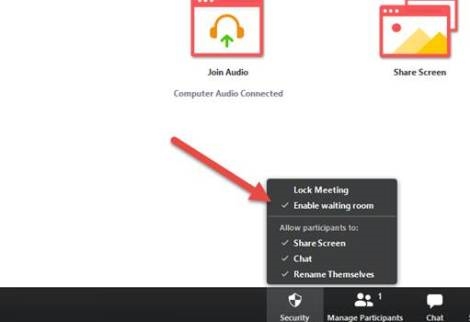
Lock Your Zoom Meetings After They Start
Once your meeting is up and running Zoom has a handy, yet seldomly used feature, which allows you to lock your meeting to future guests. This is very useful when you are certain all your expected guests have arrived since this prevents anyone else from joining the call unless the host manually allows them to enter. To lock a meeting the host simply has to select “Lock meeting” which can be found on the participant’s button at the bottom of your Zoom meeting.
Pro Tip: once enabled even people with the meeting ID and Password will not be admitted in, so if you know people are running late you should give them a heads up as they might think the meeting is running into technical issues.
Manage Participants?During Your Zoom Meeting
Depending on the size of your conference call this can be a tedious task to complete but is highly recommended. If an unwelcomed person has joined a meeting, they can quickly be removed by clicking the participant’s ID and selecting “Remove” from the dropdown menu. If by chance the same person rejoins the call, you can take further action by blocking the user which will prevent them from joining any additional calls for your entire account. This can only be done through the Zoom Web portal but provides great peace of mind.
Pro Tip: For larger meetings, the main host can nominate a co-host to manage participants on their behalf so they can focus on the meeting at hand.
Mute Zoom Participant Web cameras and Microphones Upon Entry
Unfortunately, nothing is 100% effective, but as an extra layer of safety muting guests and having web cameras disabled upon entry is a great way to reduce the impact of unwanted guests. This setting is slightly more complex than the others but a step by step guide can be found here. Muting participants upon entry can prevent anyone from speaking until the house manually unmutes them, which can be done individually or for all participants.
Pro Tip: there is a hidden setting called “Allow participants to unmute themselves” which must be disabled for this to work effectively.
Final Thoughts
As the coronavirus pandemic wages on, Zoom will continue to be a key tool for many businesses. While we lack a lot of control over what’s happening in society, you do have the control over your Zoom account and ensuring it is secure for your business.
It’s important to be aware that Zoom is making updates frequently, as a result, some of our recommendations may not be available. Different types of accounts may have different access levels and settings. The above advice can be applied to paid Zoom accounts.
Zoom continues to do a stellar job at taking the necessary steps to protect their users from potential privacy issues and data breaches. The horror stories are few and far between, but if you follow our advice, you (and your guests) should have full confidence that your meeting will remain secure.
Happy Zooming.
The post Zoom Security Best Practices – How To Avoid Zoom Bombing appeared first on Search Engine People Blog.
(13)

